What is the “Final Warning” email scam
If you receive the “Final Warning” email that threatens to release an explicit video of you watching pornography, you can ignore it. This email falls into the sextortion scam category, and all of its contents are false. There is no malware on your computer, nor is there a video of you watching pornography.
The “Final Warning” email is a classic example of a sextortion scam email. Though sextortion scam campaigns are operated by different malicious actors, the emails are all more or less identical and follow the same pattern. The emails first catch users’ attention with alarming subject lines like “Final Warning” or “You have the last chance to save your social life – I am not kidding!”, try to scare users with claims of malware on users’ computers and threaten to release non-existent explicit videos of users watching pornography.
This particular email is worded in a way that makes it seem like the sender previously tried contacting the recipient. The email goes straight to the point and claims that the recipient has 72 hours to pay $2000 if they do not want an explicit video of them to be sent to all contacts. The sender then explains that malware was downloaded onto the recipient’s computer when they visited a pornography website. The malware supposedly allowed the malicious actor complete access to the recipient’s computer, including the ability to turn the camera/microphone on/off. The sender claims to have noticed the recipient watching pornography and decided to make a video. The video supposedly shows the recipient on one side and the video they were supposedly watching on the other side. The sender threatens to release the video unless they agree to pay $2000 in Bitcoin.
It goes without saying that paying anything to these scammers would be a waste of money because the email is completely fake. Users’ computers are not infected with malware, nor is there a video of them watching pornography in the hands of cybercriminals.
Sextortion emails initially appear alarming but if users take the time to inspect them, they quickly become completely nonsensical. Scammers use various scare tactics to pressure users into paying but are rarely successful. Sextortion emails are generally written in a very mocking tone, with the sender trying to shame the user for their supposed pornography-viewing habits. However, the threat to send an explicit video to all contacts is particularly effective, even among users who have never visited pornography websites.
The full text from the “Final Warning” email scam is below:
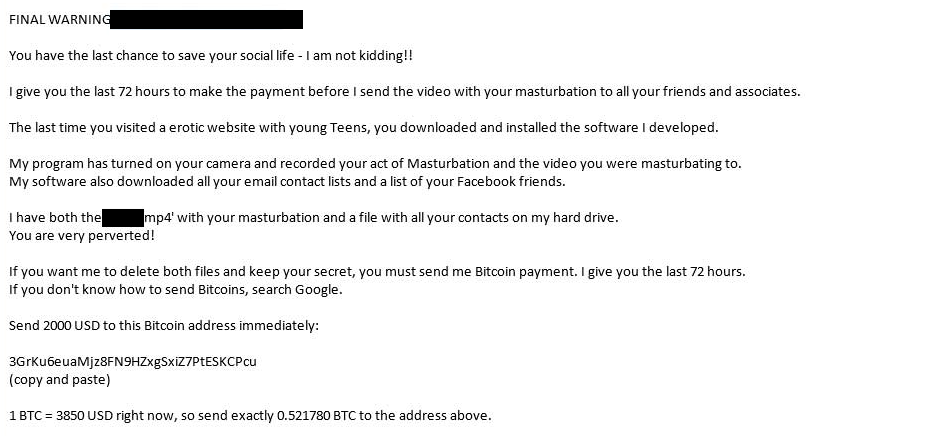
FINAL WARNING – !
You have the last chance to save your social life – I am not kidding!!
I give you the last 72 hours to make the payment before I send the video with your masturbation to all your friends and associates.
The last time you visited a erotic website with young Teens, you downloaded and installed the software I developed.
My program has turned on your camera and recorded your act of Masturbation and the video you were masturbating to.
My software also downloaded all your email contact lists and a list of your Facebook friends.I have both the – with your masturbation and a file with all your contacts on my hard drive.
You are very perverted!If you want me to delete both files and keep your secret, you must send me Bitcoin payment. I give you the last 72 hours.
If you don’t know how to send Bitcoins, search Google.Send 2000 USD to this Bitcoin address immediately:
3GrKu6euaMjz8FN9HZxgSxiZ7PtESKCPcu
(copy and paste)1 BTC = 3850 USD right now, so send exactly 0.521780 BTC to the address above.
Do not try to cheat me!
As soon as you open this Email I will know you opened it.This Bitcoin address is linked to you only, so I will know if you sent the correct amount.
When you pay in full, I will remove both files and deactivate my software.If you don’t send the payment, I will send your masturbation video to ALL YOUR FRIENDS AND ASSOCIATES from your contact list I acquired.
Here are the payment details again:
Send 0.521780 BTC to this Bitcoin address:
—————————————-
3GrKu6euaMjz8FN9HZxgSxiZ7PtESKCPcu
—————————————-You can visit the police but nobody will help you.
I know what I am doing.
I don’t live in your country and I know how to stay anonymous.Don’t try to deceive me – I will know it immediately – my spy ware is recording all the websites you visit and all keys you press.
If you do – I will send this ugly recording to everyone you know, including your family.Don’t cheat me! Don’t forget the shame and if you ignore this message your life will be ruined.
I am waiting for your Bitcoin payment.
Lavern
Anonymous HackerP.S. If you need more time to buy and send 0.521780 BTC, open your notepad and write ’48h plz’.
I will consider giving you another 48 hours before I release the vid, but only when I see you are really struggling to buy bitcoin.
Why did you receive a sextortion scam email
Sextortion email scammers always claim that users received the emails because their computers have been infected with malware. However, in reality, users receive the emails because their email addresses have been leaked. Unfortunately, data like email addresses is leaked all the time, whether because of a company’s mistake or a cyberattack. Stolen or leaked email addresses end up on hacker forums, where they are bought by other cyber criminals. So if you received this “Final Warning” email scam, your email address has likely been leaked. You can check on HaveIBeenPwned. If it has been leaked, there’s not much you can do but at least you can be more vigilant with unsolicited emails, especially if they contain an attachment or a link.
In some cases, malicious actors also reveal users’ passwords. This is an effective tactic and adds credibility to the email. In users’ minds, how else would the sender know their password if not because they hacked their computer? However, there’s a simple explanation for this. Passwords are stolen the same way as email addresses. Unfortunately, a lot of services and platforms have poor security and store passwords in plaintext, which means passwords would be stolen if a cyberattack were to happen. Just like email addresses, passwords end up on hacker forums. If you have unique passwords for each account and receive a sextortion email with a specific password, you can easily determine which service leaked it. If an extortion email ever reveals a password you use, change it immediately. Ideally, passwords should never be used twice. Passwords should also be difficult to guess, and be made up of combinations of upper and lowercase letters, numbers, and symbols. Password managers are great tools for users who struggle with creating strong passwords.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.