What is “If you want us to be silent, read” email scam
“If you want us to be silent, read” is how a new sextortion scam campaign tries to attract your attention. An email with this subject line may land in your inbox if your email address has ever been leaked, but it is nothing more than a scam. The sender will claim that they have a private video of you watching adult content but that is not true. This kind of email is merely a generic sextortion scam attempt that should be ignored.
Sextortion scam emails have been on a rise recently, with new campaigns appearing regularly. They are all more or less the same because they follow a similar pattern. The emails first try to attract attention with threatening subject lines. In this case, it’s “If you want us to be silent, read”. Other examples include “Please dont make an even more fool of yourself”, “Read before your buddies will see the other side of you”, “I am sorry to inform you but your device was hacked“, and “I have e-mailed you from your account“. The senders then claim to have a video of users watching pornography and threaten to release it online if money is not sent in Bitcoin to the shown wallet address. These sextortion attempts are generally not very successful, judging by the zero or very little amount of money transferred to the wallets. Nonetheless, it’s important to be aware of these scam campaigns to avoid becoming a victim.
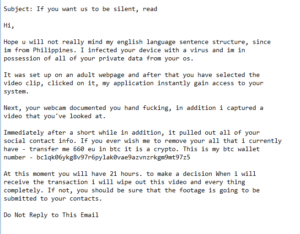
This particular sextortion scam email is written in broken English because the sender is supposedly from the Philippines. The sender proceeds to inform you that your device is infected with a virus and they are “in possession of all of your private data from your os”. Supposedly, you visited an adult website that was compromised and by clicking on a video, you initiated the download of malicious software. According to the sender, the malware allowed them to turn on the webcam and spy on you while you were watching pornography. The sender also claims to have stolen all your contacts and threatens to send a split-screen video of you watching the video plus the video itself to all your contacts. Supposedly, they will not send the video and delete it completely if you agree to pay €660 in Bitcoin. The sender gives you 21 hours to send the Bitcoin. However, despite how threatening the email may seem, there is no video, nor do you need to pay anything.
Overall, this is one of the more believable campaigns of this kind. Scammers often make up highly unlikely, even outright ridiculous scenarios to essentially blackmail users. One scam email campaign in the past claimed that an assassination hit has been ordered on the user, and it would be carried out unless they agreed to pay money. Another campaign claimed that a bomb has been placed at the user’s place of work and will go off if money is not paid. A more recent one threatened to infect users and their families with the coronavirus if they did not agree to pay. So this sextortion scam email campaign, while not particularly convincing, is at least more believable than other versions.
Generally, whenever you receive such an email, you can safely ignore it. Better yet, simply remove “If you want us to be silent, read” email scam and similar from your inbox. Certainly do not pay any money to these scammers because there is no video of you watching adult content, nor is your computer infected with any kind of malware. Unless, of course, the infection is unrelated to this.
Why did you receive this email?
Generally, sextortion scammers claim that users receive these emails because their computers have been hacked. However, in reality, it’s because their email addresses have been leaked by some service they use. Email addresses that were leaked or part of data breaches are sold on various hacking forums, where cybercriminals and scammers buy them by the thousands. They then use these email addresses to launch massive spam email campaigns. You can use haveibeenpwned to check whether your email address has even been part of some data breach. If you received one sextortion email, chances are, you’ll receive them and other types of scams in the future as well. However, as long as you are aware of what scam emails look like, you should be able to recognize them.
In some cases, sextortion emails contain users’ actual passwords. These passwords are used to make sextortion emails appear more legitimate because users may believe that their computers do contain malware if the sender is aware of the password. However, there is a good explanation for how passwords end up in the hands of scammers, and it has nothing to do with malware on a computer. Passwords are bought from hacker forums the same way email addresses are. This is why the passwords are usually old and no longer used by users.
If you receive a sextortion email and it has your password in it, your computer has not been hacked, your password has just been leaked. If it’s a password you still use, change it immediately. You should also never reuse passwords because if hackers can access one account, they could access all others that have the same passwords.
“If you want us to be silent, read” email scam removal
If this or a similar email lands in your inbox, just remove it from your inbox. Do not pay any attention to the contents and ignore all demands to pay anything. These sextortion scams are never legitimate and all claims about videos of you watching adult content are false.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.