The biggest data breaches of 2018
The biggest data breaches of 2018
2018 was the year of data breaches. Near the end of 2017, many predicted that we would see devastating ransomware attacks dominate 2018, but data breaches make up the majority of cybersecurity incidents in 2018. There were small ones affecting a couple of hundred of thousand users, and there were huge ones involving data of hundreds of millions of users.

Social media Facebook allowed a political consulting company to harvest data of 87 million users, and then a bug allowed attackers to potentially take over 30 million accounts. MyFitnessPal, British Airways, My Heritage, and Marriott were also among those to suffer severe data breaches, with the last one being particularly serious.
We have compiled a list of the most notable cybersecurity incidents, which are mainly data breaches, and it’s rather worrying to see how many people had their information leaked by companies. Let’s hope companies learn from not only their own but others’ mistakes and employ better security practices when it comes to users’ data.
Continue reading to find out more about the biggest cybersecurity incidents of 2018.
Facebook Cambridge Analytica scandal
2018 has been a rough year for social media giant Facebook, particularly after the Cambridge Analytica scandal broke. It was one of the biggest incidents of the year so it is unlikely that it is the first time you are hearing about it. But to refresh your memory, here’s what happened.
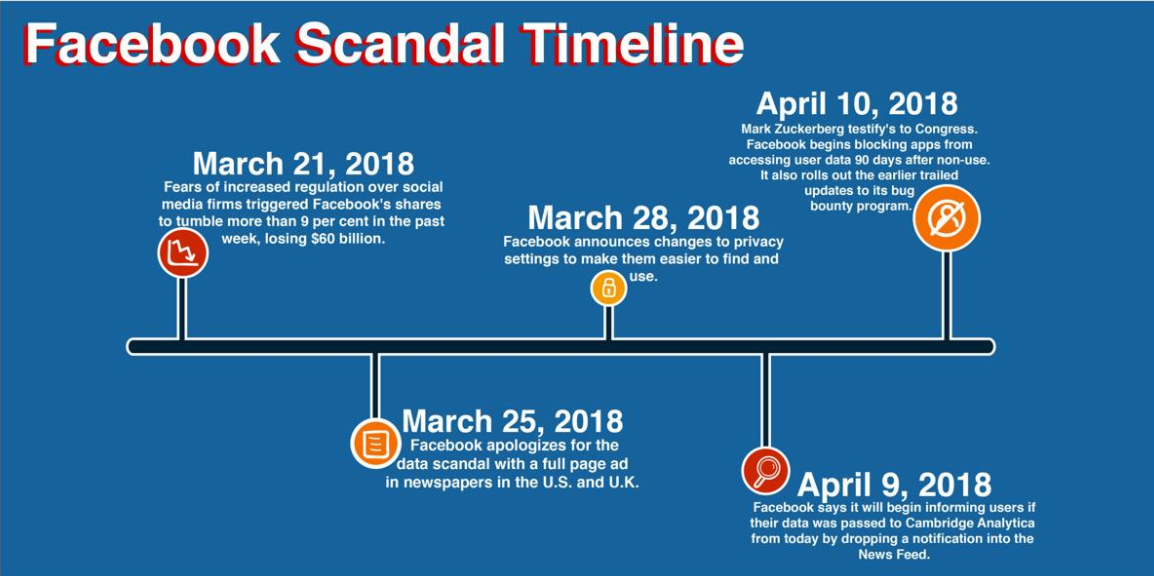
It all began when data scientist Aleksandr Kogan developed an app called “This is your digital life” (thisisyourdigitallife), which was voluntarily used by 270,000 people. The people who used the app were asked to grant access to their Facebook profiles, supposedly for academic research. However, because of Facebook’s policies at that time, if users gave the permission, they also allowed the app to access their friend lists. Therefore, in addition to gaining access to data from the 270,000 initial profiles, the app also harvested information from all public profiles in the friend lists. It is estimated that information of around 87 million Facebook profiles was handed to Cambridge Analytica this way. Reportedly, the data obtained by Cambridge Analytica was enough to create profiles to determine what kind of advertising would be most effective for certain users, for political events in particular.
Facebook has known about the data harvesting since 2015 but has chosen not to inform its users until news agencies had already broken the story. The company removed the thisisyourdigitallife app soon after it became aware of the unauthorized access and had ordered the company to erase the acquired data, but it did not take the necessary steps to ensure that Cambridge Analytica no longer possessed the data.
When the Facebook data harvesting scandal broke, it caused a huge public outcry, which eventually led to Facebook’s CEO Mark Zuckerberg testifying in the US Congress.
Facebook breach involving 30 million users
In September, Facebook revealed a breach in the network, which could have allowed attackers to take over 30 million Facebook accounts. According to Facebook, the attackers exploited a vulnerability in Facebook’s code impacting the “View As” feature, which allowed people to see what their profile looks like to other users. Exploiting the vulnerability allowed them to steal Facebook users’ access tokens, which could be used to take over users’ accounts. The tokens are what keeps users logged in to Facebook without them needing to re-enter login credentials.
It was later revealed that 15 million people had their name and contact details (phone number, email or both) accessed, while 14 million users had other details accessed in addition to the mentioned two. For the latter, the information included gender, language, religion, relationship status, current city, birthdate, education, work, etc., essentially information people had in their profiles.
“First, the attackers already controlled a set of accounts, which were connected to Facebook friends. They used an automated technique to move from account to account so they could steal the access tokens of those friends, and for friends of those friends, and so on, totaling about 400,000 people,” Facebook said in a blog post. “In the process, however, this technique automatically loaded those accounts’ Facebook profiles, mirroring what these 400,000 people would have seen when looking at their own profiles. That includes posts on their timelines, their lists of friends, Groups they are members of, and the names of recent Messenger conversations.”
According to Facebook, none of the tokens were actually used, and would not have worked in any case, as they were invalidated when the incident was announced.
Google+ data leak and closure
Back in October, Google revealed that an API bug potentially exposed private profile data of more than 500,000 Google+ users. According to Google, the bug was located in Google+ People API and it allowed 438 third-party apps to gain access to users’ private data, when generally apps can only access public profile information with users’ permission. However, the tech giant claims none of the apps were aware they had such permission, thus it was not misused. The company was unable to tell which particular users were affected.
According to Google, the bug was discovered and immediately patched in March, 2018. However, a report by Wall Street Journal claimed that not only was the API bug much worse than reported by Google, but it also could have leaked user data since 2015. The report claims that Google only discovered the leak when they started preparing for EU’s GDPR. It should be mentioned that the bug was discovered around the same time the Facebook-Cambridge Analytica scandal was making headlines all over the world, thus there are allegations that Google purposely concealed the incident in order to avoid immediate regulatory interest.
In December, Google revealed another bug, one that could have exposed the personal information of around 52.5 million Google+ users. The bug was discovered during internal tests, and resided in Google+ People API endpoint. The bug allowed certain apps to view non-public information, but according to Google, the bug was not exploited.
When the first bug was announced, Google revealed that it was closing down the consumer version of Google+ by the end of August 2019. However, after the second bug was discovered, the closure was moved to April 2019. After April, Google+ will continue to operate for enterprise customers only.
Under Armour’s MyFitnessPal data breach
In March 2018, Footwear company Under Armour revealed that attackers had stolen data of more than 150 million MyFitnessPal fitness and dietary app users. According to the company, affected information includes usernames, email addresses, and hashed passwords. What the data stolen did not include was payment card information, which is collected and processed separately. Even if the breach involved 150 million people, it could have been much worse had the app collected Social Security and driver’s license numbers.
British Airways data breach
In September 2018, airline British Airways revealed that it had suffered a data breach affecting tens of thousands of British Airways customers. Around 244,000 payment card records may have been stolen, in addition to names and email addresses. Card numbers, expiry dates and CVV numbers of 77,000 customers may have also been stolen.
In order to avoid compromising the investigation, it was not revealed how the breach happened exactly. However, the airline did reassure users that there is no evidence showing that the data was removed from their systems.
Marriott data breach
In late November, hotel chain Marriott announced a security breach that affected 500 million hotel guests. The breach dates back to 2014 but it was only noticed in September 2018. According to the hotel chain, an unauthorized party had encrypted and copied information from its database and had been preparing to remove it. Marriott were able to decrypt the information and uncover that the data was from the reservation database of Starwood hotels, which were acquired by Marriott in 2016.
It was revealed that the breach involved 500 million Starwood hotel customers, for 327 million of which the data included names, phone numbers, email and mailing addresses, passport numbers, dates of birth, gender, arrival and departure information, and reservation dates. The information also included payment card numbers and expiration dates for some number of users.
My Heritage data breach
Genealogy website My Heritage suffered a data breach that leaked information of over 92 million users. The company was informed of the leak by a security researcher who found a file containing email addresses and hashed passwords of MyHeritage users on a private server. While the company only became aware of this in June 2018, the breach took place in October 2017.
Only email addresses and hashed passwords were leaked, as other information such as family trees and DNA data are stored elsewhere. While the information exposed was not highly sensitive in the sense that it did not contain full names, Social Security numbers, phone numbers, etc., the amount of users affected is rather worrying.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
