Sextortion email scams: malicious actors threaten to expose private videos that don’t actually exist
Over the last couple of years, there has been a significant increase in sextortion scam emails threatening users with non-existent videos of them watching pornography. “I have got two not really pleasant news for you“, “If you want us to be silent, read“, “I am sorry to inform you but your device was hacked“, are just a few examples of how sextortion scam emails begin. The emails are pretty harmless but it’s understandable that they may alarm more than a few users.
 A classic example of a sextortion scam
A classic example of a sextortion scam
What is a sextortion email scam?
A sextortion email is a type of scam that falsely claims users have been filmed watching pornography videos. The senders threaten to publicly release the videos unless users agree to pay the ransom. These scams started appearing at least a couple of years ago and continue to bother users to this day. The emails are not very convincing but the subject matter is bound to make some users anxious. Though it’s difficult to measure how profitable these scams are. Some scams are able to trick a couple of victims into paying, while others receive zero payments.
Most sextortion scam emails are very generic and follow an almost identical pattern, despite being sent by different scammers. They may be worded differently but if you’ve seen one, you’ve seen them all.
Sextortion emails usually begin with a threatening line that the receiver’s reputation will be ruined. Scammers then explain that they planted malicious software on a pornography website that users visited. Supposedly, as soon as users entered that site, the malware was downloaded on their computers. According to the sextortion emails, the malware can log keystrokes, steal information, and turn on the microphone/web camera. The email then goes on to say that the malware essentially caught users watching pornography and made a video through the webcam. It’s supposedly a dual video, with the pornography video on one side and the victim watching it on the other. The malware also supposedly allowed this “hacker” to steal personal data as well as contacts for friends/colleagues/family. If the victim does not agree to pay a ransom, the video will supposedly be sent to all contacts as well as shared on the Internet.
“Otherwise, if you neglect my demand, within ninety-six h I will send ur clip to ur closest people and comrades, and I as well will distribute it to the Internet,” one generic sextortion scam email says.
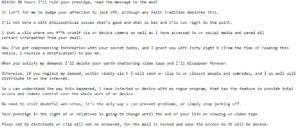 Another example of a sextortion scam
Another example of a sextortion scam
The demanded sum of money differs from one scam to another, though usually, the sum is around $1500 to be paid in Bitcoin. But no matter how threatening these emails may appear, they are all fake. There is no malware, nor is there a video. Victims who pay the demanded sum of money would essentially be paying scammers who can’t do any harm to them.
The emails are usually plain text. However, in some cases, they also contain links or email attachments. Engaging with either of those is a not good idea because users could be led to malicious sites or initiate malware on their computers.
Why do some sextortion emails contain personal information and passwords?
While in most cases, sextortion scam emails are very generic. But some scammers employ certain techniques to make them appear more convincing.
It should be mentioned that the malicious actors behind these sextortion emails obtain email addresses from various hacker forums. Victims’ email addresses end up on those forums after they are leaked by services users use. Full names are usually included along with the email addresses. This is why some sextortion emails will address victims in their full names. It’s possible to check whether an email address has been leaked in the past on haveibeenpwned.
There are also sextortion emails that contain users’ actual passwords. This can be quite convincing for some users, enough so that they would fall for the scam completely. After all, how would the sender know their password if not because they actually installed malware on the computer? The answer to that is actually quite simple. Passwords are often leaked together with email addresses. Malicious actors buy them from hacker forums, not steal them from a computer. The same haveibeenpwned site also checks whether passwords are part of any known data breaches.
If a sextortion email scam contains passwords users actually use, they need to be changed immediately. Passwords should also be unique to each account. Using the same password on multiple accounts increases the risk of getting hacked. If hackers obtain one password, they can use it to access multiple accounts. Passwords should also be complex and difficult to guess/crack. Users have the tendency to use weak passwords for their accounts, and that is one of the biggest mistakes they can make when it comes to account protection. As a general rule, a password should contain uppercase and lowercase letters, numbers, and symbols. To generate strong passwords and keep track of all of them, it’s a good idea to use a password manager. Setting up two-factor authentication is also highly recommended.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
