Remove Vgod ransomware
Vgod ransomware is file-encrypting malware that targets personal files. The malware encrypts files and essentially takes them hostage. The ransomware infection can be identified by the .Vgod extension it adds to encrypted files. None of the files with that extension will be openable unless you first decrypt them. The malicious actors operating Vgod ransomware demand that victims pay a ransom to get a decryptor necessary for file recovery. However, trying to get the decryptor will be difficult, if not impossible. At the moment, only users who have backups can recover files for free.
Once Vgod ransomware infiltrates a computer, it starts the process of encrypting files immediately. Unfortunately, its primary targets are personal files that users would be most willing to pay for, such as documents, photos, videos, and images. Encrypted files can be easily identified by the .Vgod extension added to their names. For instance, a file named text.txt would change to text.txt.Vgod. Each victim of the ransomware is assigned a unique ID, which the attackers use to distinguish between victims.
Additionally, the ransomware drops a Decryption Instructions.txt ransom note and changes the desktop wallpaper. This note informs victims that their files have been encrypted and outlines steps they can take to restore access to them. Unfortunately, recovering files typically involves paying a ransom. While the note does not specify the cost of the decryptor, it is expected to be several hundred or even thousands of dollars as that is usually what ransomware operators demand.
The ransom note dropped by Vgod ransomware is below:
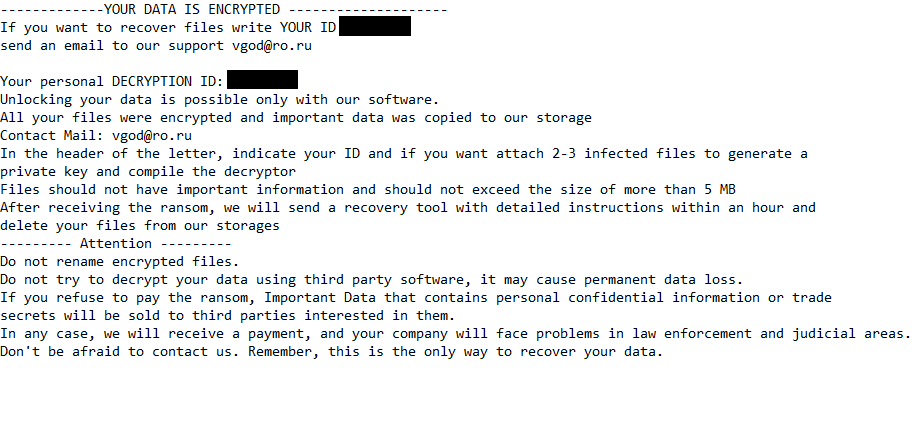
————-YOUR DATA IS ENCRYPTED ——————–
If you want to recover files write YOUR ID –
send an email to our support vgod@ro.ruYour personal DECRYPTION ID: –
Unlocking your data is possible only with our software.
All your files were encrypted and important data was copied to our storage
Contact Mail: vgod@ro.ru
In the header of the letter, indicate your ID and if you want attach 2-3 infected files to generate a private key and compile the decryptor
Files should not have important information and should not exceed the size of more than 5 MB
After receiving the ransom, we will send a recovery tool with detailed instructions within an hour and delete your files from our storages
——— Attention ———
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
If you refuse to pay the ransom, Important Data that contains personal confidential information or trade secrets will be sold to third parties interested in them.
In any case, we will receive a payment, and your company will face problems in law enforcement and judicial areas.
Don’t be afraid to contact us. Remember, this is the only way to recover your data.
Engaging with cybercriminals and paying a ransom is always strongly discouraged. Victims should remember that they are dealing with criminals who have no obligation to help them, even after a payment is made. There is no assurance that victims will receive a functioning decryptor or one at all. Many victims have previously paid ransoms only to find that the decryptors provided do not work or are never delivered.
For those with backups, file recovery will not be an issue. Users can begin file recovery as soon as they remove Vgod ransomware from their systems. It is highly recommended to use an anti-malware program, as this type of infection is quite sophisticated. Once the ransomware has been deleted, it is safe to connect to the backup. Unfortunately, for users without backups, the only course of action is to save the encrypted files and wait for a free Vgod ransomware decryptor to become available, although there is no guarantee it will be released.
How does ransomware infect computers?
Malicious actors employ various methods to spread ransomware, such as torrents, email attachments, and harmful links or ads. Generally, users who have bad browsing habits are at a higher risk of infection due to their risky online behavior. Improving these habits is an effective way to protect oneself against malware infections, as is familiarizing oneself with popular malware distribution methods.
Emails serve as a popular and convenient method for malware distribution. Malicious emails are often disguised as parcel delivery notifications or order confirmations, aiming to capture users’ attention with alarming messages about large sums of money or expensive purchases. This tactic creates a sense of urgency that can pressure users into opening attachments without verifying their legitimacy. However, a closer examination can reveal signs of malicious intent. For example, these emails frequently contain glaring grammar and spelling mistakes, which you would not usually see in legitimate emails from legitimate companies. Malicious emails also tend to use generic greetings such as “User”, “Member”, or “Customer” since scammers typically don’t have access to a recipient’s personal information. In contrast, legitimate companies tend to personalize their emails with the recipient’s name.
When malicious emails target specific high-profile people/companies, the emails tend to be significantly more sophisticated. Such emails may not have the usual signs of phishing. For example, they will address the recipient by name and include information that gives them credibility. Therefore, it’s a good idea to avoid opening unsolicited email attachments unless they have been scanned with an anti-virus program or VirusTotal.
Torrents are another widely used method for malware distribution among cybercriminals. It’s widely known that torrent sites are often poorly moderated, allowing malicious actors to upload torrents with malware in them. Those who download torrents for movies, TV shows, or video games are particularly susceptible to malware. Pirating copyrighted content is not only illegal but also jeopardizes your computer’s security and personal data.
How to remove Vgod ransomware
Ransomware is a highly sophisticated threat that requires a professional program to remove. Attempting to manually remove Vgod ransomware can lead to further damage to your device. Therefore, it is highly recommended to use an anti-virus program. Once the ransomware has been completely removed and is no longer detected, you can connect to your backup and start recovering your files. Be cautious, as connecting to your backup while ransomware is still active may result in your backed-up files becoming encrypted as well.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.