Remove VerdaCrypt ransomware virus
VerdaCrypt ransomware virus is a malicious infection that encrypts files. It’s a type of malware that essentially takes users’ files hostage by encrypting them and demands payment for their decryption. The ransomware can be identified by the .verdant extension added to encrypted files. Unfortunately, you will not be able to open files with this extension unless you first put the files through a special decryptor, which only the ransomware operators have. Unless you have a backup of your files, you may not be able to recover them.
VerdaCrypt ransomware is identifiable by the .verdant extension it appends to encrypted file names. For example, an image.jpg file would become image.jpg.verdant. This ransomware primarily targets all important files, including photos, videos, and documents, since victims are more likely to pay for those. Once the files are encrypted, a !!!_READ_ME_!!!.txt ransom note is dropped. This note, written in a very condescending and preachy tone, informs users that their files have been encrypted and can only be restored with a specific decryption tool. The criminals responsible for this ransomware do not disclose the ransom amount, stating it will only be revealed upon initial communication with the malware operators via Protonmail.
When it comes to ransomware, it is never recommended to pay the ransom, as there is no guarantee that your files will be recovered. Although the malware operators promise that they will provide the decryption tool upon payment, there is no assurance that they will fulfill this promise. Many victims who have paid ransoms in the past have not received the promised decryption tools. While the decision to pay is ultimately yours, you need to take into account the risks, particularly since the demanded amount will likely be substantial.
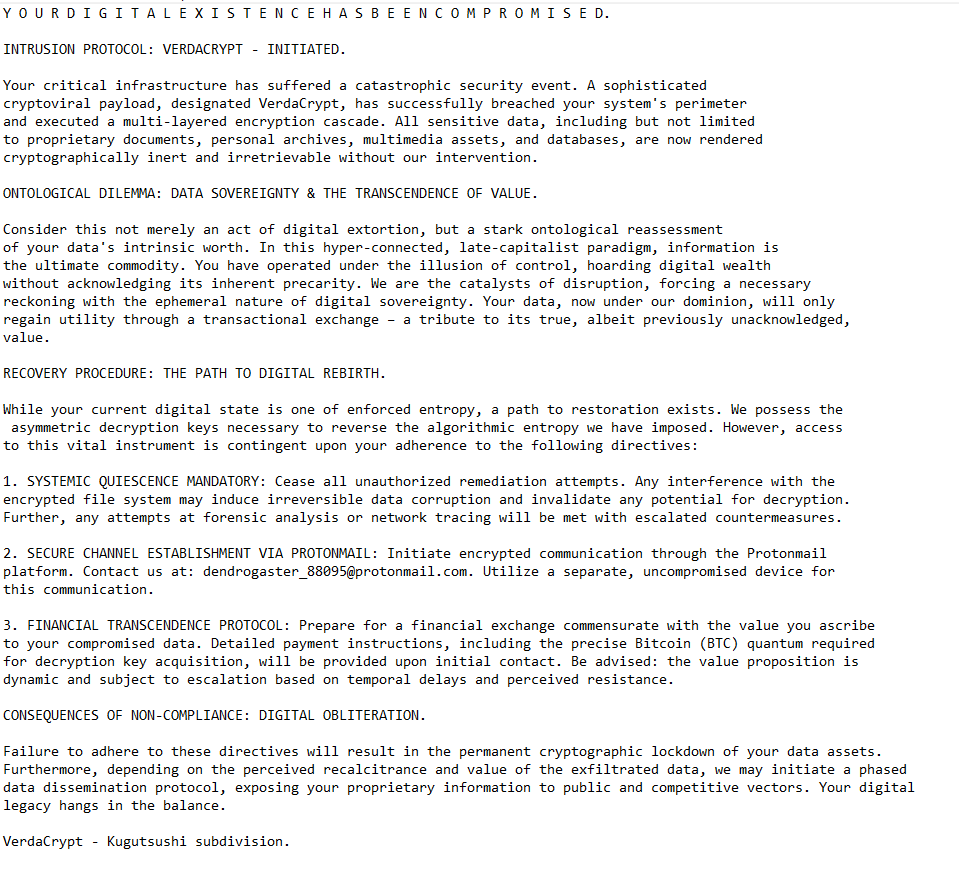
The full VerdaCrypt ransomware !!!_READ_ME_!!!.txt ransom note is below:
Y O U R D I G I T A L E X I S T E N C E H A S B E E N C O M P R O M I S E D.
INTRUSION PROTOCOL: VERDACRYPT – INITIATED.
Your critical infrastructure has suffered a catastrophic security event. A sophisticated cryptoviral payload, designated VerdaCrypt, has successfully breached your system’s perimeter and executed a multi-layered encryption cascade. All sensitive data, including but not limited to proprietary documents, personal archives, multimedia assets, and databases, are now rendered cryptographically inert and irretrievable without our intervention.
ONTOLOGICAL DILEMMA: DATA SOVEREIGNTY & THE TRANSCENDENCE OF VALUE.
Consider this not merely an act of digital extortion, but a stark ontological reassessment of your data’s intrinsic worth. In this hyper-connected, late-capitalist paradigm, information is the ultimate commodity. You have operated under the illusion of control, hoarding digital wealth without acknowledging its inherent precarity. We are the catalysts of disruption, forcing a necessary reckoning with the ephemeral nature of digital sovereignty. Your data, now under our dominion, will only regain utility through a transactional exchange – a tribute to its true, albeit previously unacknowledged, value.
RECOVERY PROCEDURE: THE PATH TO DIGITAL REBIRTH.
While your current digital state is one of enforced entropy, a path to restoration exists. We possess the asymmetric decryption keys necessary to reverse the algorithmic entropy we have imposed. However, access to this vital instrument is contingent upon your adherence to the following directives:
1. SYSTEMIC QUIESCENCE MANDATORY: Cease all unauthorized remediation attempts. Any interference with the encrypted file system may induce irreversible data corruption and invalidate any potential for decryption. Further, any attempts at forensic analysis or network tracing will be met with escalated countermeasures.
2. SECURE CHANNEL ESTABLISHMENT VIA PROTONMAIL: Initiate encrypted communication through the Protonmail platform. Contact us at: dendrogaster_88095@protonmail.com. Utilize a separate, uncompromised device for this communication.
3. FINANCIAL TRANSCENDENCE PROTOCOL: Prepare for a financial exchange commensurate with the value you ascribe to your compromised data. Detailed payment instructions, including the precise Bitcoin (BTC) quantum required for decryption key acquisition, will be provided upon initial contact. Be advised: the value proposition is dynamic and subject to escalation based on temporal delays and perceived resistance.
CONSEQUENCES OF NON-COMPLIANCE: DIGITAL OBLITERATION.
Failure to adhere to these directives will result in the permanent cryptographic lockdown of your data assets. Furthermore, depending on the perceived recalcitrance and value of the exfiltrated data, we may initiate a phased data dissemination protocol, exposing your proprietary information to public and competitive vectors. Your digital legacy hangs in the balance.
VerdaCrypt – Kugutsushi subdivision.
If you backed up your files before VerdaCrypt ransomware infected your device, you should be able to restore them without any issues. However, it should be stressed that removing the VerdaCrypt ransomware first is necessary. If you access your backup while the ransomware is still on the system, those backup files could also become encrypted. What’s more, you should not try to manually remove VerdaCrypt ransomware virus, as this may cause further damage to your computer. Using a professional anti-malware program is necessary.
There is currently no free VerdaCrypt ransomware decryptor tool available. Thus, if you do not have a backup, you may not be able to recover your files at this time. If a free VerdaCrypt ransomware decryptor does get released, it will become available on NoMoreRansom.
How is ransomware distributed?
Users who have poor online habits are often the most vulnerable to malware infections. If you regularly open unsolicited email attachments, download programs or content from unreliable sources, use torrents to pirate copyrighted content, or click on ads while browsing potentially risky websites, it’s only a matter of time before your computer is infected with some kind of infection. If you want to protect your device from future malicious infections, developing better browsing habits is essential.
If you’re using torrents to access copyrighted content, you’re likely aware that torrent sites tend to be poorly regulated. Malicious actors often target these platforms because many users don’t know how to recognize malware in torrents. They upload torrents for popular movies, video games, TV shows, and software that contain malware, and when users download and initiate it, the malware can begin its malicious activities. Keep in mind that downloading copyrighted content via torrents is not just content theft; it also significantly endangers your computer and its files.
Malicious spam emails, known as malspam, are a common method for spreading infections like ransomware. Cybercriminals buy large numbers of email addresses from various hacking forums and launch extensive spam campaigns. Many of these email addresses have been compromised due to data breaches or leaks. For those whose addresses have been leaked, most malicious emails are relatively easy to spot. However, when they are tailored to specific individuals, they can appear more sophisticated. Even the most cautious users can fall for more sophisticated malspam under the right circumstances.
Typically, generic malicious emails carrying malware contain numerous grammar and spelling errors, address recipients with words like User, Member, and Customer, and put strong pressure on opening the attached file by claiming it’s an important document that needs to be urgently reviewed. These generic malicious emails often try to mimic legitimate emails from companies, but their low-effort nature makes them easy to recognize as malicious.
Even though many malicious emails can be identified easily, it’s still essential to scan any unsolicited email attachments with anti-virus software or services such as VirusTotal before opening them.
How to remove VerdaCrypt ransomware virus
Ransomware is a highly sophisticated infection, which is why we recommend against trying to manually remove VerdaCrypt ransomware virus. Incorrect removal could allow the malware to recover, or you could cause additional damage to your device. Additionally, if it stays on your system and you connect to your backup, there’s a good chance that your backed-up files could also get encrypted. It’s best to use a reputable anti-virus program to delete VerdaCrypt ransomware for safe removal.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.