Remove “Some-one Try To Login Into Your Mailbox Address” scam email
The “Some-one Try To Login Into Your Mailbox Address” email is part of a phishing campaign that aims to steal users’ email login credentials. The email claims that someone tried to log into the recipient’s email account, and if the recipient wants to continue using the account, they need to verify their account by clicking on the provided link. If users engage with the email and click on the link, they will be taken to a phishing site and asked to type in their email login credentials. If they do, their accounts could be stolen.
This “Some-one Try To Login Into Your Mailbox Address” email is a very low-effort, generic attempt. Most users should be able to identify it as a phishing email immediately if they’re familiar with what phishing emails look like. Emails part of this phishing campaign explain that recipients’ email accounts may have been accessed by someone else. The email asks that users verify their email addresses if they wish to continue using the email account. The email contains a “Verify email address” button that recipients are asked to click to supposedly do the verification.
The full text from the “Some-one Try To Login Into Your Mailbox Address” phishing email is below:
Subject: [-]: Please confirm to continue.
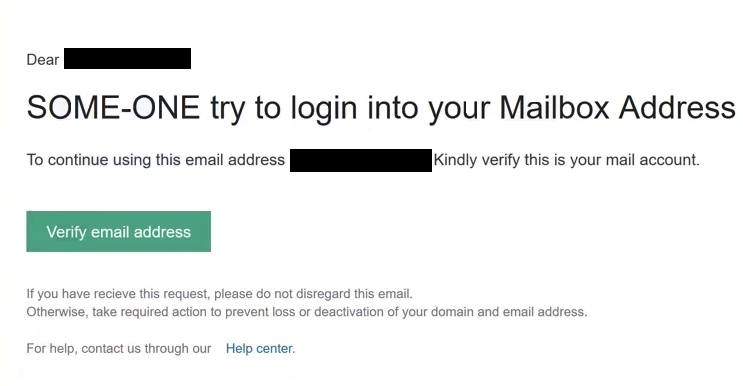
Dear –
SOME-ONE try to login into your Mailbox Address
To continue using this email address – Kindly verify this is your mail account.
Verify email address
If you have recieve this request, please do not disregard this email.
Otherwise, take required action to prevent loss or deactivation of your domain and email address.For help, contact us through our Help center.
When users click the “Verify email address” button, they are taken to a website designed to look like it’s a legitimate email service provider website. This site shows a pop-up message instructing users to log in to confirm their accounts. If users input their passwords, those details are sent directly to the cybercriminals operating this phishing scheme. The malicious actors may either exploit the stolen credentials or sell them to other cybercriminals. Email login information is particularly valuable to cybercriminals because it often contains sensitive data and is linked to multiple other accounts. A compromised email account can provide cybercriminals with access to various other accounts.
How do you recognize phishing emails?
Phishing campaigns targeting large numbers of users with the same email are usually easy to identify because they tend to be vague and generic. Generic, low-effort spam emails usually don’t have credible information and have loads of mistakes. However, if a malicious email targets someone specific, the emails would look much more sophisticated and more difficult to identify. Fortunately for most users, they will usually deal with generic phishing emails.
If you receive an unsolicited email asking you to do something (e.g. clicking a link or opening an attachment), you first need to verify the sender’s email address before doing anything. You can do this by using a search engine to check if the email address belongs to the person or organization it claims to represent. Some malicious email addresses might look suspicious, making it easier to spot potential phishing attempts. However, scammers sometimes employ tactics to mask their email addresses, such as substituting letters or adding extra characters. For example, they might add an extra “f” to an email address to mimic Netflix’s.
Grammar and spelling mistakes are also a good indication of a malicious email. Phishing emails, for whatever reason, often have a lot of mistakes. For instance, this “Some-one Try To Login Into Your Mailbox Address” scam email doesn’t have a lot of text but there are plenty of mistakes. Legitimate emails, especially from service providers, do not have these kinds of mistakes.
Users should take their time to carefully analyze emails before doing anything, especially if the email prompts them to click on links or open attachments. For example, this “Some-one Try To Login Into Your Mailbox Address” email is evidently a scam when you consider that email providers do not send notifications like that.
Lastly, we recommend not clicking on links in emails altogether. If you receive an email that claims there’s an issue with an account of yours, it’s best to go directly to the website by typing its URL into your browser, rather than following the link provided in the email. For instance, if you receive an email from Netflix regarding a missed payment, you should log into your account directly to resolve the issue instead of using the linked information from the email.
“Some-one Try To Login Into Your Mailbox Address” phishing email removal
Just delete “Some-one Tried to Login to Your Mailbox Address” email if it lands in your inbox. If you’ve already clicked on the email and entered your login information, make sure to change your password immediately, provided you can still access your account. It’s also a good idea to check your account activity for any unauthorized access.
If you can no longer access your email account, contact your email service provider for assistance. Furthermore, you need to unlink your email address from any other accounts to avoid further risks of other accounts being hacked.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.