Remove Scp ransomware
Scp ransomware is file-encrypting malware from the Makop ransomware family. The ransomware encrypts target files and demands a payment for their recovery. The malware can be identified by the .[unique ID].[studiocp25@hotmail.com].scp extension added to encrypted files. In addition to encrypting files, the ransomware also claims to have stolen the files and threatens to release them if a payment is not made.
SCP ransomware is part of the Makop ransomware family and can be recognized by the extension it appends to encrypted files. This extension is as follows: .[unique ID].[studiocp25@hotmail.com].scp. Each victim receives a unique ID to distinguish them from other victims. For instance, a file named 1.txt would be renamed to 1.txt.[unique ID].[studiocp25@hotmail.com].scp after encryption. Sadly, any files with this extension cannot be opened. This type of ransomware targets a wide range of files, including documents, images, etc., essentially everything that could contain important information that victims would either be willing to pay to get back or do not want to be published publicly.
Once the encryption process is complete, a +README-WARNING+.txt ransom note will be dropped. This note explains what has happened to the files and what victims need to do next. According to the note, files were not only encrypted but also stolen. The operators of the ransomware are demanding payment in exchange for a decryption tool. Furthermore, they threaten to release the stolen files publicly if victims refuse to pay. While the note does not specify the ransom amount, it is likely to be thousands of dollars.
The full Scp ransomware ransom note is below:
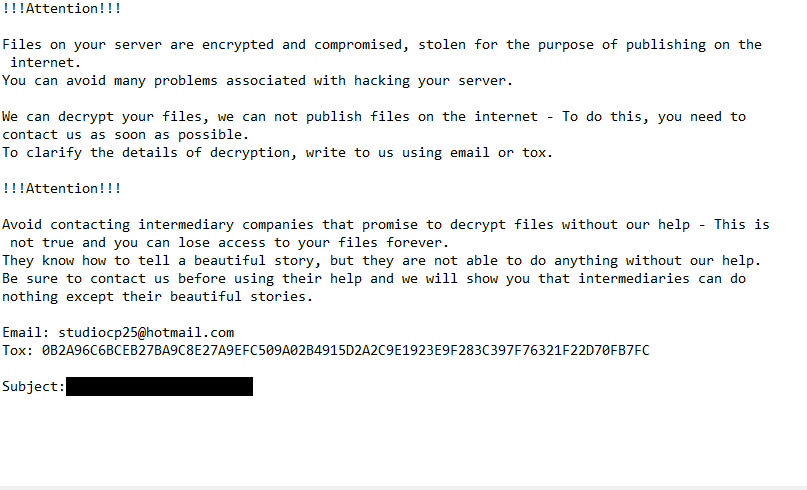
!!!Attention!!!
Files on your server are encrypted and compromised, stolen for the purpose of publishing on the internet.
You can avoid many problems associated with hacking your server.We can decrypt your files, we can not publish files on the internet – To do this, you need to contact us as soon as possible.
To clarify the details of decryption, write to us using email or tox.!!!Attention!!!
Avoid contacting intermediary companies that promise to decrypt files without our help – This is not true and you can lose access to your files forever.
They know how to tell a beautiful story, but they are not able to do anything without our help.
Be sure to contact us before using their help and we will show you that intermediaries can do nothing except their beautiful stories.Email: studiocp25@hotmail.com
Tox: 0B2A96C6BCEB27BA9C8E27A9EFC509A02B4915D2A2C9E1923E9F283C397F76321F22D70FB7FCSubject: –
When it comes to ransomware, it’s always strongly advised against paying the ransom for several key reasons. Firstly, there’s no guarantee that victims will receive a decryptor even if they do pay. Victims should always keep in mind that they are dealing with criminals who have no obligation to assist them simply because they’ve given them money. It’s also unlikely that a payment would deter malicious actors from releasing the stolen files publicly. Moreover, any payment users make will likely fund further criminal activities.
If victims have backups, they can access them to begin file recovery as soon as they remove Scp ransomware from their systems. If the ransomware is still present when the backup is accessed, files in the backup will be encrypted as well.
How does ransomware enter computers?
It’s worth mentioning that users’ bad online habits often lead to malware infections. Users with good habits are significantly less likely to come across malware because they engage in less risky behavior. Therefore, developing better online habits is essential to avoid future infections. Understanding the common methods of malware distribution is also crucial.
Being able to identify malicious emails is vital, particularly if your email address has been leaked, as you may receive such emails eventually. The same can be applied to employees in companies. One infected computer could take down the whole system. Luckily, unless users are specifically targeted, most malicious emails are fairly generic and can be easily spotted because of grammar and spelling mistakes.
Users need to watch out for vague greetings like “User,” “Member,” or “Customer” in emails, as these may indicate a potential threat or spam. Reputable companies personalize their emails by addressing users by name, while malicious actors often rely on generic terms because they don’t have access to personal information.
It’s also worth noting that targeted malicious emails can be significantly more sophisticated. These emails tend to be free of mistakes, contain credible information, and address recipients by name. To protect themselves, users should always scan all unsolicited email attachments with anti-malware software or tools like VirusTotal.
Torrents serve as another common way for malware distribution. Many torrent sites lack effective moderation, resulting in the continued upload of torrents with malware in them. Malware is often bundled with torrents for entertainment content, such as movies, TV shows, and video games. Downloading copyrighted material through torrents not only violates the law but also poses significant risks to the computer’s security.
How to remove Scp ransomware
Attempting to remove Scp ransomware manually would be a mistake as that could cause further damage to the computer. Ransomware is a complex infection that requires a professional program for effective removal. Attempting to handle it yourself poses a risk of additional harm. If you have a backup, do not connect to it until you completely remove Scp ransomware from your device.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.