Remove Sage ransomware
Sage ransomware is file-encrypting malware that targets personal files. The malware is part of the Djvu/STOP ransomware family and can be identified by the .sage extension added to encrypted files. Unfortunately, you cannot open any files with this extension unless you first use a decryptor on them, which only the malware operators currently have. Only users who have backups of their files can recover them for free.
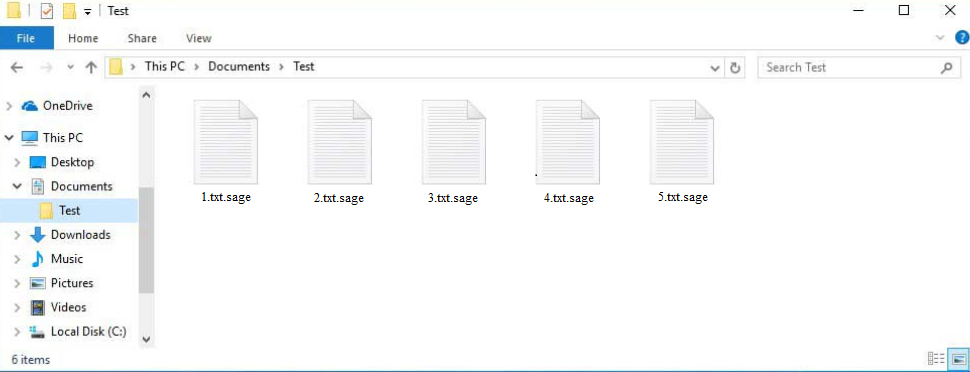
Sage ransomware is one of hundreds of Djvu/STOP ransomware versions. The malware operators release new versions regularly, and they can all be identified by the extensions they add to encrypted file names. This particular version adds .sage. For example, an encrypted 1.txt file would become 1.txt.sage when encrypted. All personal files will have this extension, including photos, videos, documents, images, etc. You will not be able to open any files that have this extension unless they are first put through a decryptor. However, getting that decryptor is not easy as only the malicious actors behind this ransomware have it.
When the ransomware is done encrypting files, it will drop a _readme.txt ransom note that contains instructions for how to get the decryptor. The note explains that files have been encrypted and that the only way to recover them is with a decryption tool. Unfortunately, unless you have a backup of your files, that is true. The cybercriminals behind this ransomware offer the decryptor for $980. The note also mentions a 50% discount for users who make contact with cyber criminals within the first 72 hours. The malicious actors also offer to decrypt one file for free as long as does not contain any valuable information.
If you do not have a backup, paying the ransom may seem like a good idea. However, you should keep in mind that paying does not guarantee a decryptor. Unfortunately, you are dealing with cybercriminals, who are unlikely to feel any kind of pressure to help victims, even those who pay. Countless ransomware victims have not received decryptors despite paying in the past. What’s more, by paying, you would be supporting future criminal activities.
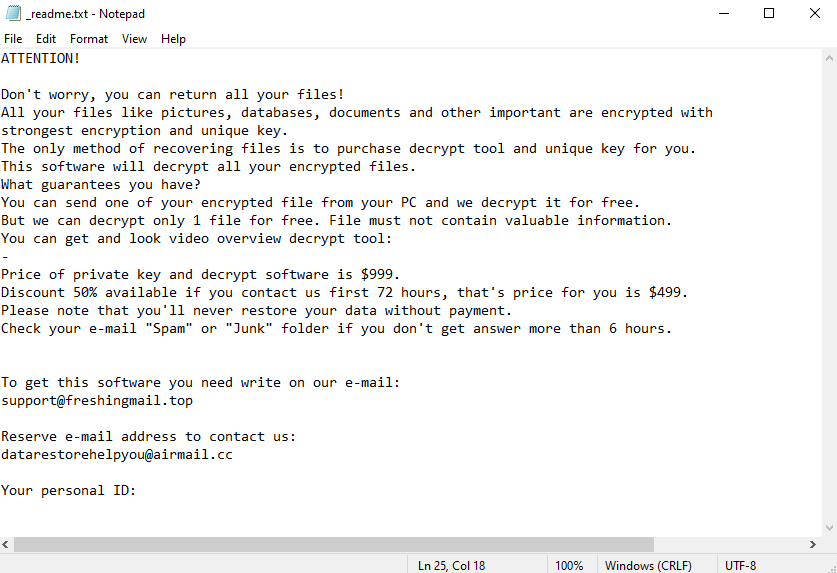
The _readme.txt ransom note dropped by Sage and other versions of this ransomware:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
manager@mailtemp.chReserve e-mail address to contact us:
helprestoremanager@airmail.ccYour personal ID:
If you have a backup, you can start file recovery as soon as you remove Sage ransomware from your computer. Make sure to use an anti-malware program to do that as ransomware is a very complex infection. Furthermore, keep in mind that if you connect to your backup while ransomware is still present on your computer, the backed-up files will become encrypted as well. If that were to happen, the files would be lost permanently.
If you do not have a backup and do not intend to pay the ransom, your only option is to back up encrypted files and wait for a free decryptor to be released. If it does get released, it will become available for download on NoMoreRansom.
How is ransomware distributed?
Users can infect their computers through various means, often due to poor browsing habits and engaging in risky online behaviors. By developing better habits and learning about common methods of malware distribution, users can significantly reduce the risk of malware infections in the future.
One prevalent way malware spreads is through email attachments. If your email address has been leaked during a data breach, you’re likely to receive malicious emails eventually. These emails may be disguised as delivery notifications or order confirmations. The malicious files attached to emails are often disguised as important documents that supposedly need to be reviewed urgently. Fortunately, many malicious emails are rather generic and thus, easy to identify. Common signs of a malicious email are grammar and spelling mistakes, which you typically won’t find in legitimate emails, especially automated ones because mistakes look very unprofessional.
When inspecting an unsolicited email, pay attention to how it addresses you. If the sender is someone who should know your name, such as a service provider but refers to you with generic words like “User,” “Member,” or “Customer”, it could indicate spam or a malicious email. Cybercriminals often send the same email to many recipients so they look very generic.
When you receive an unsolicited email that contains an attachment, make sure to scan the email attachment with an anti-virus program or VirusTotal before opening it.
Another common method for spreading malware is through torrents. Many torrent sites lack proper moderation, making it easy for malicious actors to upload infected files. This is particularly true for torrents of entertainment content such as movies, TV shows, or video games. If you decide to download pirated content, remember that you are not only engaging in theft but also putting your computer and personal data at risk.
Remove Sage ransomware
Make sure to use an anti-malware program to delete Sage ransomware from your computer. If you try to remove Sage ransomware manually, you could end up causing additional damage to your computer. Once the ransomware is gone, you can safely connect to your backup.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.