Remove REDKAW ransomware
REDKAW ransomware is a generic ransomware infection. It’s a type of infection that takes users’ files hostage by encrypting them. Encrypted files become unopenable, and ransomware operators demand payment for a decryptor. Unfortunately, if your files have been encrypted and have the .redkaw file extension, you may not be able to recover them. At the moment, only users who have backups can recover files for free. Malicious actors behind this ransomware will offer a decryptor but buying it is not recommended.
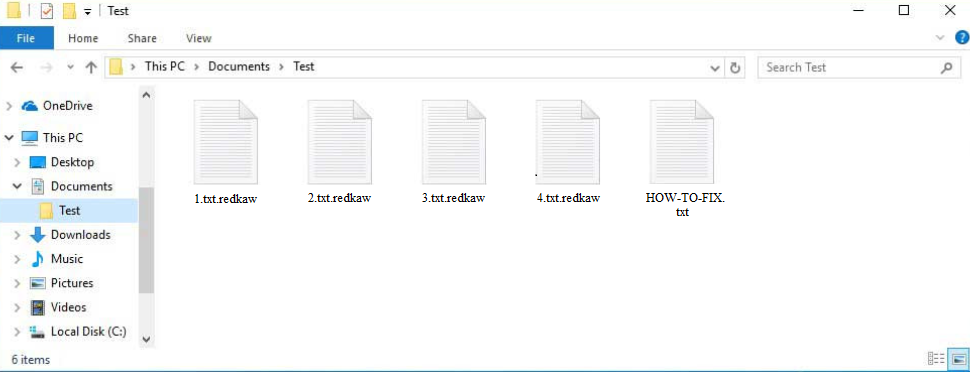
REDKAW ransomware poses a significant threat as its main targets are personal files and recovering them is not necessarily possible. It specifically targets documents, photos, videos, and other important files. Once encrypted, these files will have a .redkaw extension added to them. For example, a 1.txt file would change to 1.txt.redkaw if encrypted. Files with this extension cannot be opened until a decryptor is used.
Along with the ransomware, a ransom note titled “HOW-TO-FIX.txt” is created, informing victims that their files have been encrypted and demanding a payment of $50 for a decryptor. The note provides multiple wallet addresses for the payment and warns that victims have just 24 hours to comply; otherwise, the data may be published on an online forum.
The HOW-TO-FIX.txt ransom note is below:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
R E D K A W
YOUR SYSTEM HAS BEEN COMPROMISED!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~Your files have been encrypted and all your private information has been stolen. If you don’t take action now, your entire digital world will be destroyed.
—————————————–
Ransomware ID: REDKAW-2024-USS33993FW0
—————————————–— What has happened:
– All your documents, photos, databases, and files have been encrypted with an unbreakable encryption algorithm.
– Sensitive information, such as passwords, browsing history, private data, and any other relevant content, has been extracted and stored on a secure server.— What you need to do:
To recover your data and avoid the massive leak of your information, you must pay a ransom of **$50 USD** to one of the following cryptocurrency wallets:Bitcoin Wallet:
3MEi6jfVxHuTVSAs8EcmCvSt46b3Yyj4CdEthereum Wallet:
0x5546a6c439Cb82aBe7C4F168532c46FDA1CF56fFLtc:
MC2mAUyTpvN59CdjNwLFfXgXReonMqgykEUSDC:
0x3f0B164163Ca4ca34ccd629083a6854B5d63Eee8USDT:
0xA405f18958C9761234856611b680410b0B7c2d16You have **24 hours** to complete the payment. If time runs out, your data will be published on dark web forums, leading to public exposure of your activity and digital life.
— Why you can trust us:
– Reputation: Our credibility is our highest priority. If we don’t provide the decryption key after payment, no one will trust us again. We have attacked multiple systems and no victim has been dissatisfied after paying.
– Guarantee: If you pay, you will immediately receive the instructions and the key to decrypt your files.— How to contact:
Send a email to:* gniomhara@proton.me
After the payment
— Warning:
* Do not attempt to delete the ransomware or modify the encrypted files; any attempt to do so will result in permanent data loss.
* If you choose to ignore this message, our backdoors will allow us to return and repeat the attack. Do not underestimate our control over your network.~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Remember: This is your only warning. Pay the ransom and save your information.
Time is running out. Don’t play with fire.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Paying the ransom is generally never recommended for several reasons. Firstly, there’s no guarantee that you will receive a decryption tool even if you do pay. Remember, you are dealing with cybercriminals, and they have no obligation to keep their end of the deal. Additionally, paying the ransom only serves to support their future criminal activities.
If you have backups of your files, you should have no issues with file recovery. However, you must first remove REDKAW ransomware from your system. If the ransomware is still present when you connect to your backup, the backed-up files will become encrypted as well. Use a good anti-malware program to delete REDKAW ransomware, as ransomware infections are very complex. Attempting to manually remove REDKAW ransomware may lead to further problems.
How is REDKAW ransomware distributed?
Malicious actors use all kinds of tactics to distribute ransomware, including torrents, email attachments, and misleading links or advertisements. Users who have poor online habits are particularly susceptible to infections, as they often engage in risky behavior. Developing better online habits is a great way to avoid malware infections. Users should also be aware of common malware distribution methods.
One very common method for spreading malware is through emails. These malicious emails are often disguised as notifications for package deliveries or order confirmations. To trick users into opening the attachments, they frequently mention large amounts of money or significant purchases, creating a false sense of urgency. Fortunately, spotting these malicious emails is usually not difficult. They typically have noticeable grammar and spelling mistakes, which you would not find in legitimate emails. Another sign is recipients being addressed with generic words like “User”, “Member”, or “Customer”. Legitimate companies always use recipients’ names when corresponding with customers since they have access to personal information.
Targeted phishing emails can be trickier to identify, as they tend to be more sophisticated. Such emails may use the recipient’s name, do not have grammar/spelling mistakes, and contain credible information. Therefore, it’s recommended to refrain from opening unsolicited email attachments until they’ve been scanned with an anti-virus program or checked for malware using VirusTotal.
Torrents are another common means of malware distribution. It is well-known that torrent sites can pose risks due to poor moderation, allowing malicious actors to upload torrents that may contain malware. Torrents featuring entertainment content—such as movies, TV shows, and video games—often come with malware. Thus, by frequently downloading copyrighted content from torrent sites, you not only engage in piracy but also put your computer and personal data at risk.
How to remove REDKAW ransomware
Ransomware is a highly complex type of malware, which is why it’s crucial to use an anti-virus program to remove REDKAW ransomware. Once you’ve successfully removed the ransomware from your system, you can safely connect to your backup and begin recovering your files. However, if the ransomware remains on your computer while you access your backup, files in the backup will also become encrypted.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.