Remove Play ransomware
Play ransomware is file-encrypting malware, operated by a notorious group of cybercriminals. Play ransomware is often associated with Russian cybergroups, and is known to target various businesses and critical infrastructure organizations in Europe, Australia, North America, and South America. This ransomware is known for its double extortion attacks, as it not only encrypts files but also threatens to publicly release them if a ransom is not paid by the victim business/organization.
Play ransomware was first detected in 2022, and since then, there have been over 300 attacks targeting businesses and organizations in several parts of the world, particularly Europe and the Americas. It appears that its primary targets are finance, law enforcement, logistics, legal, software, and shipping companies/organizations, usually midsized. Play ransomware operators use a double extortion tactic to get victim businesses/organizations to pay, and not only encrypt data but also steal it. Ransomware that only encrypts data is no longer as profitable because potential victims often have backups and file recovery plans that allow them to return to regular operations in a relatively short amount of time after a ransomware attack. Ransomware that not only encrypts files but also steals them is much more likely to receive a ransom payment because companies certainly do not want their highly sensitive data to be published/sold.
Play ransomware’s dark web data listings (Source: X)
Upon successfully infiltrating a system, the infection will first exfiltrate sensitive data before deploying the ransomware to encrypt files. Victims’ files are archived and uploaded to file-sharing sites. Once files have been exfiltrated, the ransomware proceeds with file encryption using a hybrid AES-RSA encryption.
Files with the following extensions are targeted by Play ransomware:
- .$er
- .4dd
- .4dl
- .abcddb
- .abs
- .abx
- .ac
- .accdb
- .accdc
- .accde
- .accdr
- .accdt
- .accdw
- .accft
- .adb
- .ade
- .adf
- .adn
- .adp
- .alf
- .anb
- .aq
- .arc
- .ask
- .bak
- .bcp
- .bdf
- .btr
- .cat
- .cdb
- .ckp
- .cma
- .cpd
- .crypt
- .crypt1
- .crypt10
- .crypt12
- .crypt14
- .crypt15
- .crypt5
- .crypt6
- .crypt7
- .crypt8
- .crypt9
- .dacpac
- .dad
- .daschema
- .dat
- .db
- .db-shm
- .db-wal
- .db2
- .db3
- .dbc
- .dbcrypt
- .dbcrypt8
- .dbf
- .dbs
- .dbt
- .dbv
- .dbx
- .dcb
- .dct
- .dcx
- .ddl
- .dlis
- .dp1
- .dqy
- .dsk
- .dsn
- .dtsx
- .dxl
- .eco
- .ecx
- .edb
- .epim
- .exb
- .fcd
- .fdb
- .fic
- .fm5
- .fmp
- .fmp12
- .fmpsl
- .fol
- .fp3
- .fp4
- .fp5
- .fp7
- .fpt
- .frm
- .gdb
- .grdb
- .gwi
- .hdb
- .his
- .hjt
- .ib
- .ibd
- .icg
- .icr
- .idb
- .ihx
- .itdb
- .itw
- .jet
- .jtx
- .kdb
- .kexi
- .kexic
- .kexis
- .ldf
- .lgc
- .log1
- .luminar
- .lut
- .lwx
- .maf
- .maq
- .mar
- .mas
- .mav
- .maw
- .mdb
- .mdf
- .mdn
- .mdt
- .mpd
- .mrg
- .mud
- .mwb
- .myd
- .myi
- .ndf
- .ns2
- .ns3
- .ns4
- .nsf
- .nv
- .nv2
- .nwdb
- .nyf
- .odb
- .oqy
- .ora
- .orx
- .owc
- .p96
- .p97
- .pan
- .pdb
- .pdm
- .pnz
- .qry
- .qvd
- .rbf
- .rctd
- .rod
- .rodx
- .rpd
- .rsd
- .sav
- .sbf
- .scx
- .sdb
- .sdc
- .sdf
- .sdy
- .sis
- .spq
- .sql
- .sqlite
- .sqlite3
- .sqlitedb
- .te
- .temx
- .tmd
- .tps
- .trc
- .trm
- .udb
- .udl
- .usr
- .v12
- .vis
- .vpd
- .vvv
- .wdb
- .wmdb
- .wrk
- .xdb
- .xld
- .xmlff
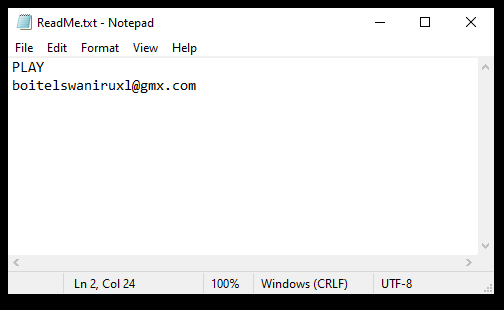
Encrypted files get the .play extension added to them. Once file theft and encryption are complete, the ransomware then drops a ReadMe.txt ransom note. The ransom note does not include a specific payment demand or an explanation for what happened, rather victims are requested to contact the cybercriminal group to get instructions via email.
Ransom notes dropped by Play ransomware always contain very little information, with its operators seemingly preferring to force victims to initiate contact first before they are informed about any demands. Ransom demands are also unique to each victim, with bigger targets likely receiving larger ransom demands, depending on how much sensitive data the ransomware was able to steal.
One example of a Play ransomware ransom note is below:
PLAY
boitelswaniruxl@gmx.com
Other variations of the note may also include links to Tor networks, but aside from that, they are always very brief and contain practically no information.
Whether to pay the requested ransom is always a debatable topic. Generally, paying is not recommended, whether the victim is an individual user or a large business/organization. There are no guarantees when it comes to ransomware gangs, considering malicious actors have no obligation to keep their end of the deal. And if they threaten to release stolen sensitive information, as is the case with Play ransomware, they may do it anyway, whether a ransom payment is made or not. After all, there is a lot of money to be made by selling companies’ data. Furthermore, large payments, in particular, encourage malicious actors to continue their malicious activities and even expand them.
Play ransomware is also currently available as a Ransomware-as-a-Service (RaaS), with cybercriminals offering the ransomware to other malicious actors as well. This allows even less sophisticated and unskilled malicious actors to operate very dangerous tools to target vulnerable businesses and organizations.
There are certain steps businesses and organizations can take to lessen the chances of becoming a victim of Play ransomware. It’s strongly recommended to remedy all known and exploited vulnerabilities, enable multi-factor authentication (especially for access to important/critical systems), update software and all applications, and regularly assess vulnerabilities.
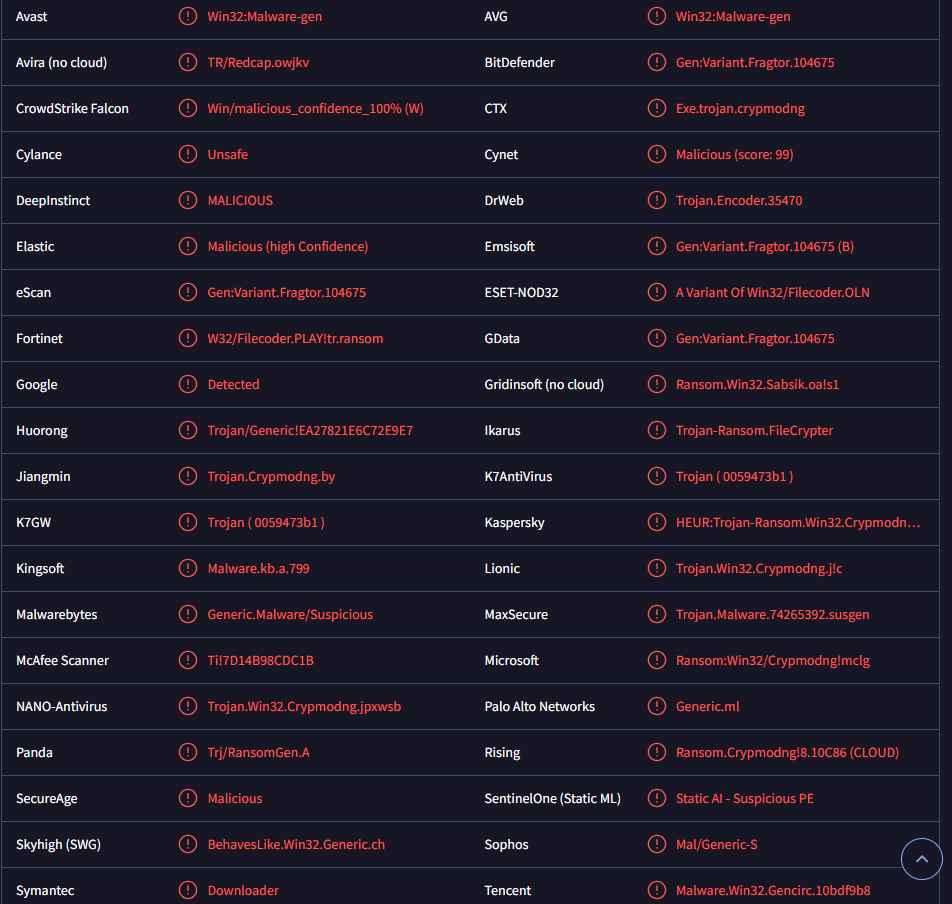
Anti-virus program detections of Play ransomware
How does Play ransomware infect systems
Play ransomware appears to only target very specific targets. The operators may use different tactics to infect a system, depending on the target. They may abuse stolen account credentials to gain access or exploit public-facing applications. Specifically, Play ransomware often took advantage of known vulnerabilities in FortiOS (CVE-2018-13379 and CVE-2020-12812) and ProxyNotShell vulnerabilities in Microsoft Exchange (CVE-2022-41040 and CVE-2022-41082). It has been noted that Play ransomware operators use both repurposed and custom tools in their attacks.
Notable Play ransomware-related attacks
It is estimated that Play ransomware has affected over 300 companies and organizations worldwide.
Globalcaja, a major bank in Spain became a victim of Play ransomware in 2023. The bank has over 300 offices in Spain and around 500,000 customers who use their services. The Play ransomware gang publicly took responsibility for the attack and stole a large amount of confidential information, including client and employee documents, contracts, passports, etc. The attack did not affect the bank’s regular operations as the bank had security protocols created for these scenarios. It is not, however, known whether the ransom was paid.
Another incident involved a Swiss IT firm. The successful attack on the IT firm resulted in affected federal and cantonal government departments. That included the Swiss army, police, and the Federal Office of Police. What’s more, data from the Federal Office of Police and the Federal Office for Customs and Border Security was stolen and published on a dark web forum.
US-based global communications firm Polycom also became a victim of Play ransomware in May 2023. According to the malicious actors, they were able to steal 600GB of data, which included highly personal information, employee documents, social security numbers, passports, IDs, financial information, budget details, etc.
In August 2022, Argentina’s Judiciary of Cordoba was targeted by Play ransomware, which resulted in the IT systems, databases, and online portals being temporarily shut down.
US semiconductor supplier Microchip Technology appears to have also been targeted by Play ransomware. On August 21, 2024, Microchip reported that its operations were disrupted by a cyberattack. On August 27, the Play ransomware cybercriminals started to leak data allegedly stolen from Microchip. Around 5GB of personal information, client documents, employee information, IDs, contracts, accounting, payroll, and taxes were leaked.
Several US cities, including Oakland, California, and Lowell, Massachusetts were targeted by Play ransomware. Oakland, California, initially had 11GB of data leaked in March 2023, including city employees’ data, police information, city files, etc. It’s reported that over the following two months, around 610GB of stolen data was leaked. The attack also disrupted regular city operations. Lowell, Massachusetts was targeted in April 2023. The city’s networks, servers, and other systems were disrupted by the ransomware attack. The ransomware gang also stole personal data, government IDs, departmental documents, financial files, and budgets.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.