Remove Hudson ransomware virus
Hudson ransomware is a file-encrypting malware. It’s a dangerous infection because it encrypts files and demands that victims buy a decryptor to get them back. The ransomware can be recognized by the .hudson extension added to all encrypted files. Unfortunately, you will not be able to open any encrypted files unless you first decrypt them. Unfortunately, that is not going to be easy, as only the malicious actors operating this ransomware have it. At the moment, only users who have backups of their files can recover them for free.
Like all ransomware, Hudson ransomware will target all personal files, including photos, videos, documents, and more. After encryption, all affected files will have an extension added, which will include your unique ID followed by .hudson. For example, an encrypted text.txt will become text.txt.{your unique ID}.hudson. You won’t be able to open any of these files unless you obtain a decryptor.
A README.TXT ransom note is dropped once the ransomware has finished encrypting files, and it explains how users can recover their files, specifically how users can purchase the decryptor. This note does not specify the ransom amount, but victims who want to buy the decryptor are instructed to contact the ransomware operators using the provided email address.
The full README.TXT ransom note is below:
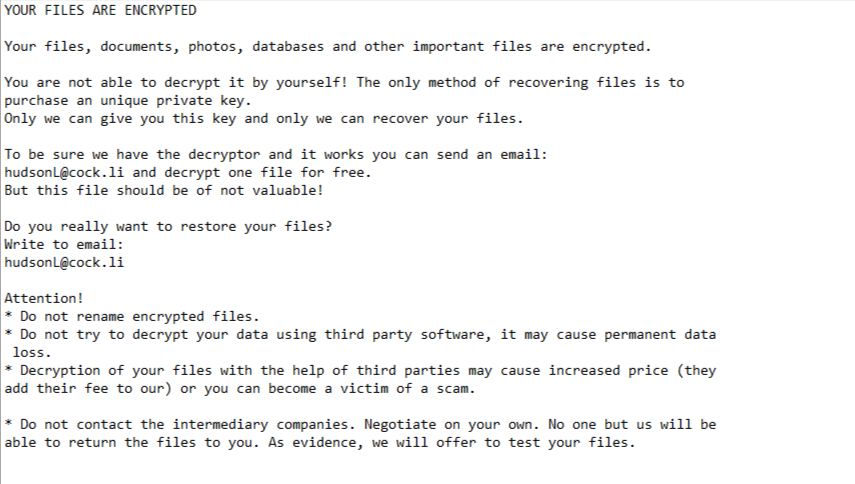
YOUR FILES ARE ENCRYPTED
Your files, documents, photos, databases and other important files are encrypted.
You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key.
Only we can give you this key and only we can recover your files.To be sure we have the decryptor and it works you can send an email:
hudsonL@cock.li and decrypt one file for free.
But this file should be of not valuable!Do you really want to restore your files?
Write to email:
hudsonL@cock.liAttention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.* Do not contact the intermediary companies. Negotiate on your own. No one but us will be able to return the files to you. As evidence, we will offer to test your files.
If you do not have a backup, paying the ransom may seem like a good idea. And while the decision to pay the ransom is yours, we strongly advise against it due to the associated risks. One important thing to keep in mind is that paying does not guarantee you will receive a working decryption tool. Since you are dealing with cybercriminals, they could easily take your money without sending the promised decryptor. This has happened many times to ransomware victims.
For those who regularly back up their important files, recovering files shouldn’t be too difficult. However, it’s essential to completely remove Hudson ransomware from your system first. If you try to connect to your backup while the ransomware is still infecting your device, it could encrypt those files as well. What’s more, you need to use an anti-malware program to delete Hudson ransomware from your device, as manual removal could cause more issues if you don’t know what you’re doing.
How did ransomware enter your computer?
Malicious actors often use emails to distribute malware. This method does not require much effort, so it’s convenient for cybercriminals. They purchase leaked email addresses, write a semi-convincing email, add the malicious attachment, and mass send the email. Out of thousands of users, there are bound to be several who will open the malicious file, thus infecting their computers. Fortunately, by learning to recognize malicious emails, you can greatly decrease your chances of falling victim to a malware infection.
For whatever reason, malicious emails often contain a lot of grammar and spelling mistakes, which are very obvious because senders usually claim to be from reputable companies whose services you use. Malicious emails typically address recipients with generic words like “User,” “Member,” or “Customer,” rather than using their names. On the other hand, legitimate emails from companies whose services you use will not have any mistakes and will address you by the name provided at registration. However, it’s worth mentioning that some malicious spam can appear quite sophisticated, so it’s always a good idea to scan any unsolicited email attachments with anti-virus software or VirusTotal before opening them.
Illegally downloading copyrighted content through torrents is not only content theft but also exposes your computer and personal data to unnecessary risks. Torrent sites are often poorly regulated, making it easy for cybercriminals to upload harmful files disguised as torrents for popular movies, TV shows, video games, or software. For example, torrents for newly released films, like a Marvel movie, frequently have malware.
These examples illustrate just a few common methods of distributing ransomware. Infections can also arise from downloads from untrustworthy sources, clicking on deceptive ads, or visiting high-risk websites. By developing safer browsing habits, you can significantly reduce your risk of encountering malware in the future.
How to remove Hudson ransomware
Because ransomware is a sophisticated infection, it’s important to use a reliable anti-virus program to remove Hudson ransomware. Make sure to use a dependable program to delete Hudson ransomware virus. Also, do not connect to your backup until you have confirmed that the ransomware is completely removed to prevent your backed-up files from becoming encrypted as well.
Once the ransomware has been removed, you can start restoring your files from the backup. If you don’t have a backup, one option is to save the encrypted files and wait for a free decryptor to be released. A useful site for finding free decryptors is NoMoreRansom. If you can’t find it there, it’s unlikely you will find it anywhere else.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.