Remove Hero ransomware virus
Hero ransomware is malware that encrypts files. It comes from the Proton ransomware family, and can be identified by the .[hero77@cock.li].hero77 extension it adds to files it encrypts. The ransomware targets all important file types, including documents and images. Unfortunately, you will not be able to open encrypted files unless you first use a decryptor on them, which only the ransomware operators have. If you have a backup of your files, you should not have any issues with file recovery. However, if backup is not available, file recovery may not be possible at this time, as even paying the ransom does not guarantee a working decryptor.
Hero ransomware is a very serious threat because it primarily targets personal files and can make their recovery impossible. It specifically targets documents, photos, videos, and other files that many users hold most important. Once these files are encrypted, the .[hero77@cock.li].hero77 extension will be added to them, which will allow you to recognize which files have been affected. For example, a 1.txt file would become 1.txt.[hero77@cock.li].hero77 after encryption. These files cannot be opened until a decryptor is used on them.
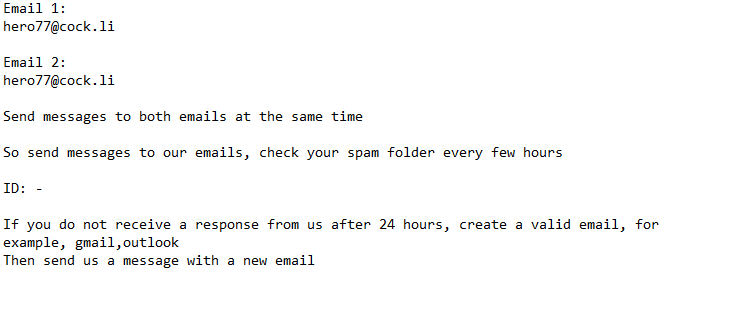
The ransomware drops a #Read-for-recovery.txt ransom note once it’s done encrypting files. The note is very brief, only mentions two email addresses and instructions to send an email to both with the unique ID included in the note. While the exact cost of the decryptor is not mentioned in the note, it is expected to be at least several hundred dollars.
The #Read-for-recovery.txt ransom note is below:
Email 1:
hero77@cock.liEmail 2:
hero77@cock.liSend messages to both emails at the same time
So send messages to our emails, check your spam folder every few hours
ID: –
If you do not receive a response from us after 24 hours, create a valid email, for example, gmail,outlook
Then send us a message with a new email
Paying the ransom after a ransomware attack is generally not recommended for a number of reasons. First and foremost, there’s no guarantee that you will receive a decryption tool even if you make the payment. Keep in mind that these are cybercriminals you’re dealing with, and they have no legal obligation to deliver on their promises. Furthermore, paying the ransom only funds their future criminal activities.
If you have backups of your files, recovering them should be easy. However, it’s important to first remove Hero ransomware from your system to prevent your backed-up files from becoming encrypted as well. It’s best to use a reputable anti-malware program to delete Hero ransomware virus, as these infections can be quite complicated. Attempting to manually remove the ransomware might lead to additional issues.
How is Hero ransomware distributed?
Malicious actors use various tactics to spread ransomware, such as uploading infected torrents, sending malware as email attachments, and promoting malicious links or advertisements. Users with poor online habits are particularly vulnerable to these infections, as they often engage in risky behaviors. Developing better online habits is an effective way to steer clear of malware threats. Users need to familiarize themselves with common methods of malware distribution as well.
A very common method of spreading malware is through email attachments. These harmful emails can be disguised as notifications for package deliveries or order confirmations. To entice recipients into opening attachments, the emails often mention large sums of money or significant purchases, instilling a false sense of urgency that can force users to act without double-checking anything. Fortunately, identifying these malicious emails isn’t usually difficult. They commonly contain noticeable grammar and spelling mistakes, which you would never find in legitimate emails from legitimate companies. Additionally, the use of generic words like “User,” “Member,” or “Customer” instead of users’ names can be a red flag, as companies typically address customers by their names in their communications.
Targeted malicious emails, however, can be more challenging to recognize. These emails are usually more sophisticated; they might include the recipient’s name, not have any grammar or spelling mistakes, and mention information that gives the email more credibility. Therefore, it is advisable to avoid opening unsolicited email attachments until they have been scanned with an anti-virus program or checked for malware using services like VirusTotal.
Torrents also serve as a common method for distributing malware. It’s not a secret that torrent sites can be risky due to their poor moderation, which allows malicious actors to upload torrents that may carry malware. Torrents for popular entertainment content—such as movies, TV shows, and video games—often come bundled with malware. By regularly downloading copyrighted content via torrents, you not only engage in piracy but also expose your computer and personal data to significant risks.
How to remove Hero ransomware
Ransomware is a sophisticated form of malware, making it essential to use an anti-virus program to remove Hero ransomware. After successfully removing the ransomware from your device, you can then connect to your backup and start restoring your files. However, be cautious; if the ransomware is still present on your computer when you access your backup, it can encrypt the files in there as well.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.