Remove Held ransomware
Held ransomware is a type of malware that encrypts files. It comes from the Djvu/STOP ransomware family. The malicious actors behind this ransomware family release new versions regularly, and Held ransomware is one of the more recent ones. The versions can be differentiated by the extensions they add to encrypted files. This ransomware adds .held to all files it encrypts. Unfortunately, files with this extension will not be openable unless you first use a decryptor on them. However, obtaining a decryptor is not easy as the malicious actors are the only ones who have it, and they will not just give it to you. At the moment, only users who have backups can recover files for free.
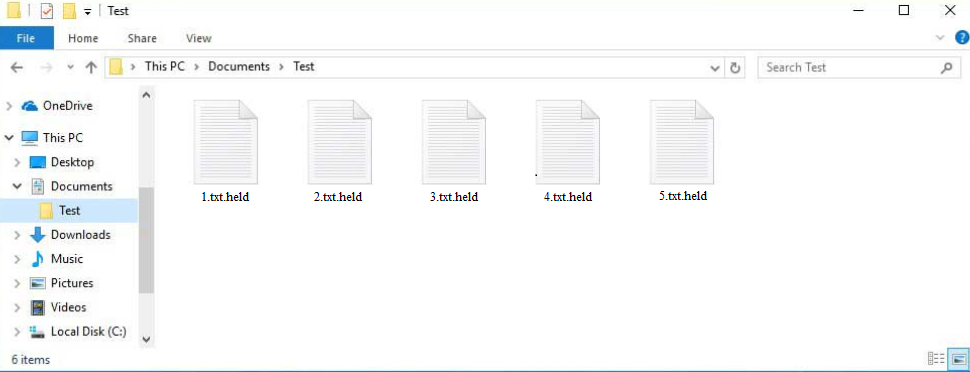
Held ransomware will target all personal files and essentially take them hostage by encrypting them. Like most ransomware, it specifically targets users’ personal files, including photos, videos, documents, images, etc., essentially all files users would be willing to pay to get back. You will be able to tell which files have been affected by the .held extension added to encrypted files. For example, an encrypted text.txt file would become text.txt.held. Files with that extension will be unopenable unless they are first decrypted with a specialized tool that only the malware operators have.
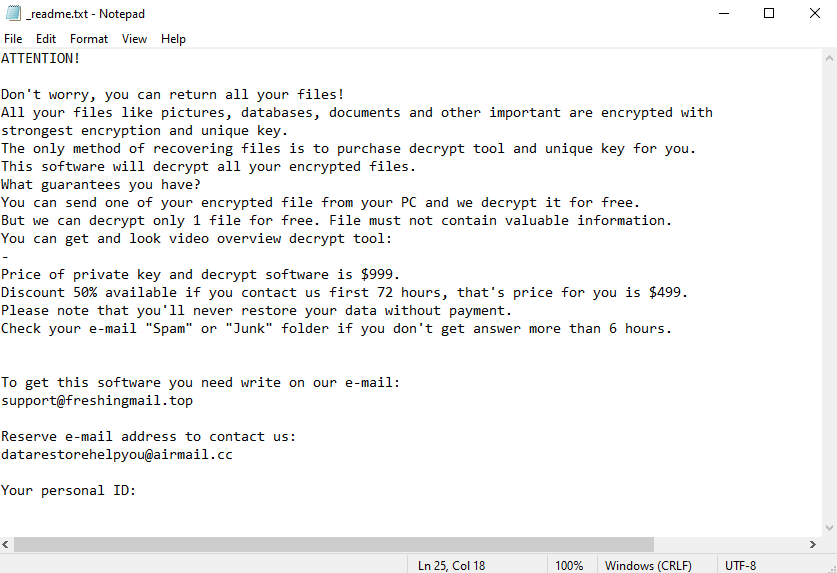
When the ransomware is done encrypting files, it drops a “_readme.txt” ransom note. The note contains instructions for how to acquire the decryptor. Unfortunately, you would have to buy it. The cybercriminals are currently selling it for $999 but promise a 50% discount to victims who make contact within the first 72 hours. Victims are also informed that they can recover one file for free as long as it does not contain any important information.
When it comes to paying the ransom, it’s never recommended for several reasons. Firstly, and perhaps most importantly, paying the ransom does not guarantee a decryptor. You need to keep in mind that you are dealing with cyber criminals and there is nothing to force them to keep their end of the deal even if you pay. Unfortunately, many victims who have paid in the past did not receive their decryptors as cybercriminals are not trustworthy. What’s more, users who pay are essentially supporting future criminal activities and making this business very profitable for malicious actors.
If you have a backup, you can connect to it and start recovering files as soon as you remove Held ransomware from your computer. It’s strongly recommended to use an anti-malware program because it’s a very complex infection that requires a professional program to get rid of. Once the ransomware is gone, you can safely connect to your backup. If you do not have a backup, your only option is to wait for a free Held ransomware decryptor to be released. Whether it gets released is not certain but if it does, it will become available on NoMoreRansom.
Ransomware distribution methods
Emails are frequently used as a method for distributing malware. Cybercriminals try to imitate emails sent by legitimate companies to trick users into engaging, specifically to open malicious email attachments. For instance, they may send fake package delivery notifications or order confirmations. In these emails, malicious actors often pressure users by stating that the attached files are important documents requiring urgent attention. If users open these malicious attachments, the malware is triggered.
Typically, it’s not too difficult to identify malicious emails since they are often generic. One of the most obvious indicators of a malicious email is grammar and spelling mistakes, which are usually not present in emails sent by legitimate senders as they appear unprofessional. The way an email addresses you can also provide clues about its legitimacy. If a sender refers to you as a User, Member, Customer, etc., rather than using your name, this should raise suspicion, as companies typically use customers’ names when contacting them. Malicious actors usually have access to limited personal information, often just an email address, which means they are forced to use generic terms.
Malicious emails can be much more sophisticated when specific users are targeted. These emails tend to be free of mistakes, include credible information, and generally look more professional and believable. For this reason, users should exercise caution with all unsolicited emails that contain attachments. It’s advisable to scan all unsolicited attachments with anti-virus software or tools like VirusTotal before opening them, just to be safe.
Additionally, malicious infections are quite prevalent on torrent websites due to their lack of strict moderation. It’s not uncommon for torrents for entertainment content—such as movies, TV shows, and video games—to contain malware. If you choose to download copyrighted content through torrents, remember that you’re not only essentially stealing content but also compromising the safety of your computer and data.
Remove Held ransomware
Because ransomware is a very serious infection, it’s strongly recommended to use an anti-malware program to remove Held ransomware. If you try to delete Held ransomware manually, you could end up causing additional damage to your device. Once your anti-malware program is successful with Held ransomware removal, you can connect to your backup and start recovering files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.