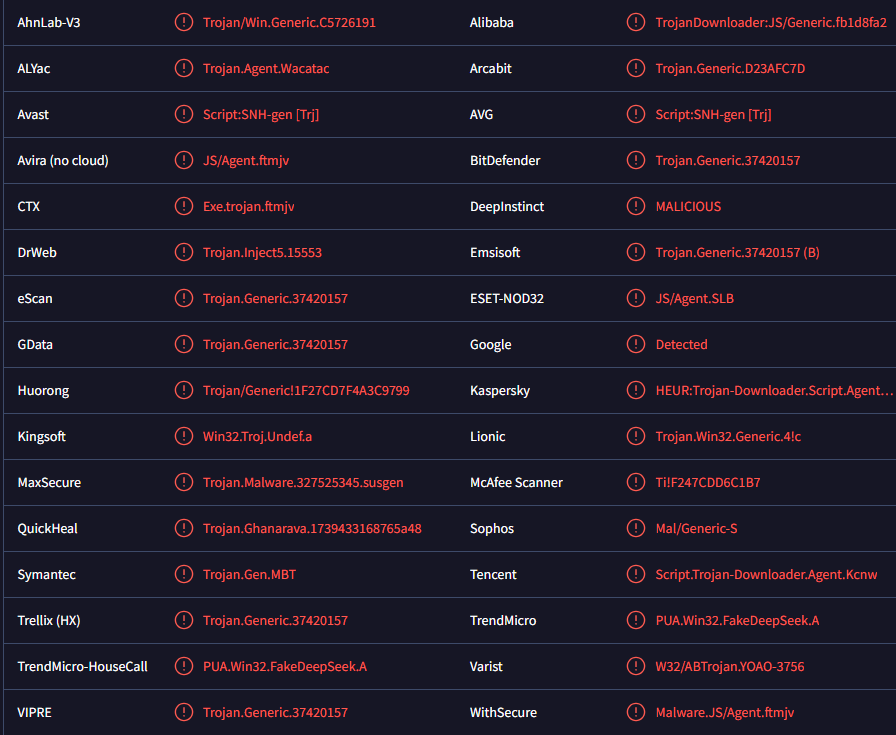
Remove DeepSeek trojan
The DeepSeek trojan is an infection that impersonates DeepSeek AI to spread. The trojan is after cryptocurrency and will stay hidden in the background while trying to steal data. While it has limited functionality at the moment, it’s still a very dangerous infection.
The DeepSeek trojan is primarily spread through fake DeepSeek websites. DeepSeek is an AI chatbox developed by a Chinese company. The malicious actors behind this DeepSeek trojan are misusing DeepSeek’s popularity to infect computers. It goes without saying that the company is in no way related to this trojan.
At the moment, the trojan’s main target is cryptocurrency wallets. It will attempt to steal cryptocurrency wallet data, which could lead to malicious actors being able to access the wallets and steal the funds.
The thing about these types of trojans is that they try to avoid detection as much as possible. Some malware infections immediately make themselves known but data-stealing infections stay hidden. If an anti-malware program is not installed on the device, it would be hard for users to notice its presence. Some signs may give it away but users would need to be very attentive. Those signs include weird processes in the Task Manager, programs crashing without an apparent reason, the computer acting sluggishly, and Internet connection issues.
Use an anti-malware program to remove DeepSeek trojan, and once it’s gone, make sure to secure your crypto accounts to prevent financial loss.
How is the DeepSeek trojan distributed?
This particular trojan is primarily distributed via a fake DeepSeek website. The fake site closely mimics the legitimate one, and users who do not pay close attention may download the malicious installer. Users may encounter links to the fake DeepSeek website on various poorly moderated forums and social media sites. Users need to be very careful when downloading popular programs as there are many sites imitating their official ones.
Trojans are also spread via other methods, such as email attachments, malicious torrents, ads, etc. Users who have good browsing habits are significantly less prone to malware infections since they take more precautions while online. Developing better online habits is a great way to avoid trojans and other forms of malware in the future.
One common method for spreading malware is through email attachments. It’s crucial to learn how to spot harmful emails. These emails often have malicious files attached to them and they’re disguised as correspondence from trustworthy companies. Opening such attachments can lead to infections, and if the malware aims to steal data, users might not even realize they’ve been compromised. Generally, a lot of malicious emails tend to be quite generic unless they are specifically tailored to their targets. Generic phishing emails are significantly easier to spot than personalized sophisticated ones. Generic ones frequently have numerous spelling and grammar errors that immediately stand out, especially since the sender pretends to be from a legitimate company/business. For instance, they might mimic order confirmations or delivery notifications, but the obvious mistakes reveal that they’re not legitimate.
Moreover, malicious emails often address recipients with generic words like User, Member, or Customer. In contrast, reputable companies typically use customers’ names in their correspondence. Since malicious actors usually don’t have access to detailed personal information, they resort to these generic greetings. If you receive an unsolicited email from a company that should know your name but addresses you with a generic term, it’s likely spam or a harmful email.
It’s important to understand that targeted malicious emails can be much more sophisticated. These emails may not have any mistakes, include credible information, and address recipients directly by name as they have access to a target’s personal information. To protect yourself from accidentally opening harmful files, always scan unsolicited email attachments with anti-malware software or services like VirusTotal.
Additionally, malware can often be found in torrents. Many torrent sites lack proper moderation, which allows malicious actors to upload infected torrents. Entertainment-related torrents, such as movies, TV shows, and video games, are particularly likely to have malware. Users should be aware that downloading copyrighted materials for free is not only content theft but also carries significant risks due to possible malware exposure.
How to remove DeepSeek trojan
To remove DeepSeek trojan, you need to use an anti-malware program. Its presence on your computer may not even be noticeable without it. At the moment, the DeepSeek trojan is specifically after cryptocurrency wallet data. If this trojan was present on your device and you use cryptocurrencies, you need to secure your wallets immediately in order to avoid losing your funds.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.