Remove Core (Makop) ransomware
Core (Makop) ransomware is malware that encrypts files. It’s a type of infection that essentially takes users’ personal files hostage and demands payment for their recovery. Core (Makop) ransomware comes from the Makop ransomware family and can be identified by the .[corecrypt@hotmail.com].core extension that gets added to all encrypted files. Unfortunately, encrypted files cannot be opened unless they are first decrypted using a special decryptor. However, obtaining the decryptor is not going to be easy as only the malicious actors operating this ransomware have it, and they won’t just give it to you.
Core (Makop) ransomware comes from the Makop ransomware family, identifiable by the file extension it adds to encrypted files. This extension is as follows: .[unique ID].[corecrypt@hotmail.com].core. Every victim is assigned a unique ID so the cybercriminals can differentiate them. For example, a 1.txt file would become 1.txt.[unique ID].[corecrypt@hotmail.com].core once encrypted by this specific ransomware. Unfortunately, files with this extension become unopenable. This ransomware targets various file types, including documents and images, essentially anything that may contain information that victims would either pay to recover or wish to keep confidential.
After the encryption process is complete, a +README-WARNING+.txt ransom note is created. The note informs the victim of the situation regarding their files and outlines the next steps. The note states that not only have the files been encrypted, but they have also been stolen. The ransomware operators demand payment in exchange for a decryption tool and threaten to publish the stolen files publicly should the victims refuse to pay. The ransom amount is not explicitly mentioned but one could expect to be asked to pay several thousand dollars.
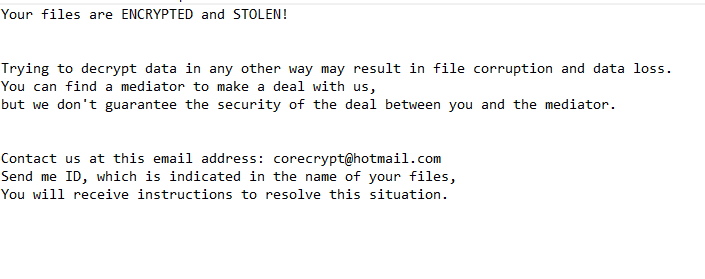
The full Core (Makop) ransomware ransom note is below:
!i!i!i!i!i!i!i!i!i!!i!i!i!i!i!i!i!i!i!i!i!i!i
Your files are ENCRYPTED and STOLEN!
Trying to decrypt data in any other way may result in file corruption and data loss.
You can find a mediator to make a deal with us,
but we don’t guarantee the security of the deal between you and the mediator.Contact us at this email address: corecrypt@hotmail.com
Send me ID, which is indicated in the name of your files,
You will receive instructions to resolve this situation.
When it comes to ransomware, paying the ransom is generally not recommended for several reasons. First and foremost, there’s no assurance that paying will result in you receiving a decryption tool; victims are essentially dealing with criminals who have no legal obligation to help them after payment. Additionally, making a payment is unlikely to stop cyber criminals from potentially releasing stolen information to the public. Furthermore, any money paid will finance future criminal activities.
If victims have backups available, they can start recovering files as soon as they remove Core (Makop) ransomware from their systems. However, it’s essential to ensure that the ransomware is completely removed before accessing these backups, as accessing them while the ransomware is still active will result in those files being encrypted as well. If that were to happen, they would be lost permanently. To ensure that the ransomware is fully removed, users need to use an anti-malware program to remove Core (Makop) ransomware.
How does ransomware enter computers?
It’s important to note that poor online habits can lead to malware infections. Users who practice safer online behavior are much less likely to encounter malware, which is why it’s important to develop better habits to prevent future infections. Additionally, being aware of the common ways malware spreads is essential.
Being able to recognize malicious emails is very important, especially if your email address has been compromised, as it’s a common malware distribution method. This also applies to employees within organizations, as one infected device could put the entire system at risk. Fortunately, unless users are specifically targeted, most malicious emails tend to be fairly generic and can be identified by noticeable grammar and spelling errors. Another thing to look out for is users being addressed by generic words like “User,” “Member,” or “Customer” in emails, as these can signal a potentially malicious or spam email. Reputable companies usually personalize their emails by using the recipient’s name, while malicious senders often resort to generic words because they don’t have their personal information.
We should also mention that more sophisticated tailored malicious emails usually don’t have mistakes, include credible information, and address recipients directly by name. To protect against these threats, users should always scan unsolicited email attachments with anti-malware software or services like VirusTotal.
Another common method for malware distribution is through torrents. Many torrent sites are not effectively moderated, allowing malware-infected files to be uploaded frequently. Often, malware is bundled with torrents for entertainment content, such as movies, TV shows, and video games. Downloading copyrighted content via torrents not only theft but also significantly jeopardizes the computer’s security.
How to remove Core (Makop) ransomware
Manually trying to remove Core (Makop) ransomware is not a good idea as it could lead to further issues with your computer. Ransomware is a sophisticated type of infection that requires the use of professional ant-malware programs for proper removal. Attempting to remove it on your own will only increase the risk of further damage. If you have a backup, it’s important that you avoid connecting to it until you fully remove Core (Makop) ransomware from your system.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.