Remove Cloak ransomware
Cloak ransomware is file-encrypting malware that essentially takes files hostage and demands payment for their recovery. The malware targets personal files because they are the ones users are usually willing to pay for. The ransomware can be identified by the .crYpt extension it adds to encrypted files. If your files suddenly have that extension, you will not be able to open them unless you first use a decryptor on them. However, acquiring the decryptor is not going to be easy because only the ransomware operators have it.
Cloak is a type of ransomware that targets personal files such as photos, videos, and documents. Once activated by opening a malicious file, it immediately begins encrypting your files. You can easily identify the encrypted files because they will have the .crYpt extension added to their file names. For example, a file named 1.txt would change to 1.txt.crYpt. Unfortunately, these files cannot be accessed without a decryptor, which is not easy to get.
After completing the encryption process, the ransomware will drop a”readme_for_unlock.txt” ransom note. This note explains the steps victims need to follow to obtain the decryptor, which involves paying a ransom. While it doesn’t specify an exact amount, it is likely to be in the hundreds of dollars. Victims are requested to download the TOR browser to access the indicated website. The operators of the malware offer to decrypt two unimportant files for free.
Below is the full Cloak ransomware ransom note:
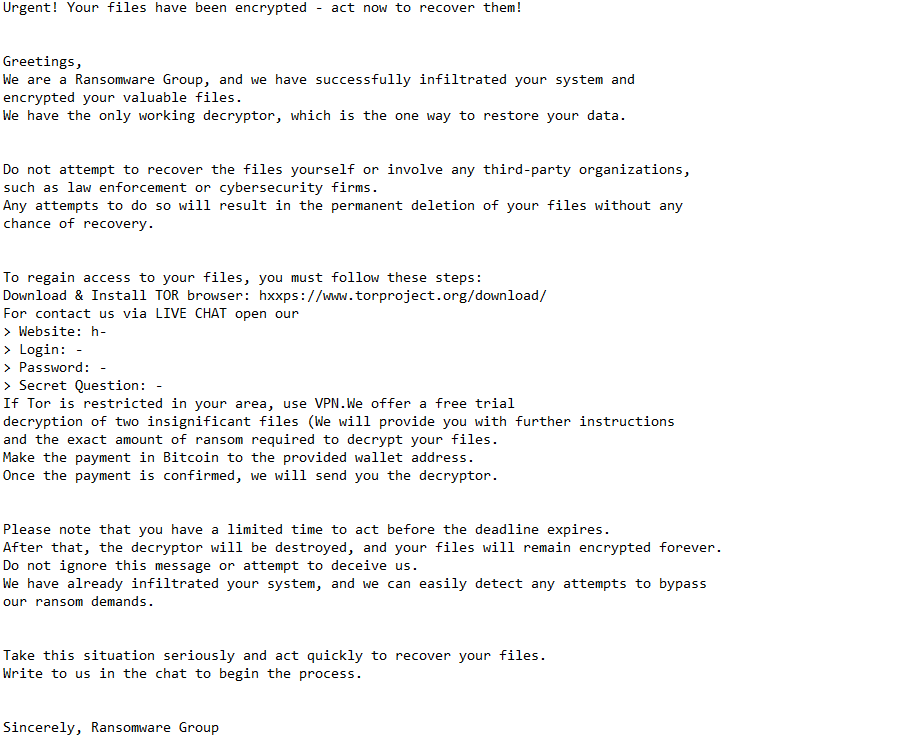
Urgent! Your files have been encrypted – act now to recover them!
Greetings,
We are a Ransomware Group, and we have successfully infiltrated your system and encrypted your valuable files.
We have the only working decryptor, which is the one way to restore your data.Do not attempt to recover the files yourself or involve any third-party organizations, such as law enforcement or cybersecurity firms.
Any attempts to do so will result in the permanent deletion of your files without any chance of recovery.To regain access to your files, you must follow these steps:
Download & Install TOR browser: hxxps://www.torproject.org/download/
For contact us via LIVE CHAT open our
> Website: –
> Login: –
> Password: –
> Secret Question: –
If Tor is restricted in your area, use VPN.We offer a free trial decryption of two insignificant files (We will provide you with further instructions and the exact amount of ransom required to decrypt your files.
Make the payment in Bitcoin to the provided wallet address.
Once the payment is confirmed, we will send you the decryptor.Please note that you have a limited time to act before the deadline expires.
After that, the decryptor will be destroyed, and your files will remain encrypted forever.
Do not ignore this message or attempt to deceive us.
We have already infiltrated your system, and we can easily detect any attempts to bypass our ransom demands.Take this situation seriously and act quickly to recover your files.
Write to us in the chat to begin the process.Sincerely, Ransomware Group
Before you make a decision about what to do next, it’s crucial to understand that paying a ransom is never a good idea. Even if you do pay, there’s no guarantee that you’ll receive the decryption key. You’re dealing with cyber criminals who have no obligation to fulfill their end of the deal once payment is made. Additionally, the money paid often funds future criminal activities that may target you again.
Cloak ransomware should not be removed manually; it’s very important to use a reliable anti-malware program to eliminate it. Once you remove Cloak ransomware, you can safely access your backups to start recovering your files. If you haven’t backed up your files, your recovery options become very limited. The only remaining choice is to back up the encrypted files and hope for a free Cloak ransomware decryptor to become available, but there’s no guarantee that such a decryptor will be released.
Ransomware distribution methods
Cloak ransomware spreads through the same methods commonly used by other malware. Users can unintentionally infect their computers by opening malicious email attachments, downloading infected torrents, clicking on harmful links, and more. Those who engage in risky online behaviors are at a higher risk of picking up malware. Developing better online habits is an effective way to prevent future infections.
A major way ransomware gets distributed is through email attachments. If your email address has been compromised, you may be more susceptible to receiving these malicious emails as your email address has been sold on various hacker forums. Fortunately, many of these emails are generic and easier to spot. They often contain numerous grammar and spelling mistakes, which stand out because the senders impersonate legitimate companies. For example, a malicious email might pretend to be a notification for parcel delivery or an order confirmation but contain loads of mistakes. That would be an immediate giveaway as legitimate emails usually avoid such mistakes as they aim to maintain a professional image. So, if you receive an unexpected parcel notification filled with mistakes, it’s likely a scam or malicious email.
Another warning sign of a potentially harmful email is the sender who should know your name addressing you as “User,” “Member,” or “Customer,” rather than using your name. For example, order confirmation emails typically address customers by their registered names. Generic greetings can signal a possible scam or malware attempt, as malicious senders often use generic words because they don’t have access to a lot of personal information.
It’s important to note that when malicious actors specifically target someone, their emails tend to be more sophisticated. Thus, always scan any unsolicited email attachments with anti-virus software or a service like VirusTotal.
Torrents are also a frequent method for distributing malware. Many torrent sites lack good moderation, allowing harmful content to be uploaded easily. Malware is especially common in popular entertainment torrents, such as movies, TV shows, and video games. While choosing to download pirated content is a personal decision, you need to recognize that this not only involves content theft but also significantly jeopardizes the security of your device and data.
How to remove Cloak ransomware
Cloak ransomware is a highly sophisticated form of malware, and attempting to remove it manually is not advisable. Without a thorough understanding of the removal process, you could unintentionally cause more harm to your computer. For this reason, it is strongly recommended to use anti-malware software to safely remove Cloak ransomware. Keep in mind that simply removing the ransomware won’t decrypt your files; a specific decryptor will be required for that.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.