Remove CipherLocker ransomware
CipherLocker ransomware is malware that takes files hostage by encrypting them. The ransomware targets personal files and makes them unopenable. Encrypted files will have the .clocker extension added to them, and the extension is how the ransomware can be identified. Unfortunately, to be able to open the files, you will need to use a decryptor on them. However, getting the decryptor is not going to be easy because only the malicious actors operating the ransomware have it, and they will not give it to you so easily.
CipherLocker ransomware poses a serious threat as it specifically targets personal files. It primarily encrypts the files users hold most important, such as documents, photos, videos, and images. When files are encrypted, a .clocker extension is added to file names. For example, the file 1.txt would change to 1.txt.clocker. These encrypted files cannot be opened without using a decryptor. The criminals typically provide instructions on how to obtain the decryptor in the ransom note.
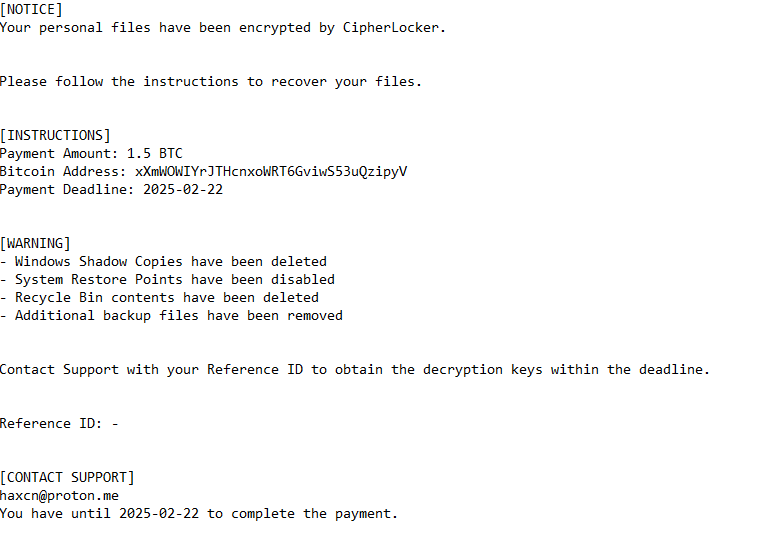
You will find a “README.txt” ransom note once the files have been fully encrypted. It informs victims their files have been encrypted and states that a payment of 1.5 BTC (approximately $100,000 at the time of writing) is required to receive the decryptor. The note includes a wallet address for payment and specifies a deadline.
The README.txt ransom note is below:
[NOTICE]
Your personal files have been encrypted by CipherLocker.Please follow the instructions to recover your files.
[INSTRUCTIONS]
Payment Amount: 1.5 BTC
Bitcoin Address: xXmWOWIYrJTHcnxoWRT6GviwS53uQzipyV
Payment Deadline: 2025-02-22[WARNING]
– Windows Shadow Copies have been deleted
– System Restore Points have been disabled
– Recycle Bin contents have been deleted
– Additional backup files have been removedContact Support with your Reference ID to obtain the decryption keys within the deadline.
Reference ID: –
[CONTACT SUPPORT]
haxcn@proton.me
You have until 2025-02-22 to complete the payment.
Paying a ransom is never recommended for several reasons, no matter what the ransomware is. Firstly, there’s no guarantee that the criminals will provide a decryptor after receiving payment. Keep in mind that you’re dealing with cybercriminals who have no obligation to give you anything in return for your money. Additionally, paying the ransom only serves to fund future criminal activities. In this specific situation, the ransom amount is so outrageous that it’s unlikely anyone would actually pay it.
If your files have been encrypted but you have a backup of your files, you can connect to it and begin the recovery process. However, it’s essential to first remove CipherLocker ransomware from your system. Using an anti-malware program is a good idea since ransomware is a sophisticated threat. Attempting to manually delete CipherLocker may result in further damage.
How is CipherLocker ransomware distributed?
There are several tactics that cybercriminals employ to infect users’ computers with ransomware, such as using torrents, email attachments, and misleading links or advertisements. Users who have very poor online habits are more susceptible to infections due to their tendency to engage in risky activities. If you take the time to develop better online habits and become familiar with the most common malware distribution methods, you will be able to avoid a lot of malware infections in the future.
Malicious emails are a common malware distribution method. Often disguised as notifications about parcel deliveries or order confirmations, these emails are designed to capture users’ attention by mentioning expensive purchases or large amounts of money. This creates a false sense of urgency for the recipient to open the attachments. Fortunately, recognizing these emails is generally not difficult, as they often contain noticeable grammar and spelling mistakes that you would never see in legitimate emails. Furthermore, malicious emails typically address recipients with generic words such as “User,” “Member,” or “Customer,” while legitimate companies will use their customer’s names. For example, if you receive a legitimate order confirmation, you will be addressed by name.
Targeted phishing attempts can be more challenging to identify, as they tend to be more sophisticated and credible. Sophisticated emails often address the recipient by name, do not have mistakes, and contain information that enhances their credibility. For this reason, avoid opening unsolicited email attachments until they have been scanned with an anti-virus program or checked for malware through services like VirusTotal.
Additionally, torrents are also used for malware distribution. Torrent sites are notorious for their poor moderation, allowing cybercriminals to upload files that may carry malicious software. Torrents related to entertainment, including movies, TV shows, and video games, frequently have malware in them. If you frequently download copyrighted content via torrents, you’re not only stealing content but are also putting your computer and data at serious risk.
How to remove CipherLocker ransomware
Ransomware is a very sophisticated infection, which is why it’s essential to use an anti-virus program to remove CipherLocker ransomware. After successfully removing the ransomware, you can safely connect to your backup to start recovering your files. However, if the ransomware remains on your system when you access your backup, the files you have stored will also become encrypted.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.