If you got a phishing email that tried to blackmail – what should you do
What are sextortion scam emails
Once in a while there is a surge of the so called sextortion scam emails (also known as porn blackmail scam emails) that want your Bitcoin. The emails are written in bad English, claim to have a video of you watching adult content, threaten to send the video to all your contacts, and demand Bitcoin in exchange for silence about your supposed porn viewing habits. Needless to say, the porn blackmail emails are nothing more than a poor attempt to scam people.
The sextortion emails are all essentially the same, though they may be worded differently. To catch your attention, scammers first reveal a password of yours. It’s usually passwords, but we have seen phone numbers used as well. They then proceed to tell you how they hacked your device/account and what kind of information they have supposedly stolen from you (it’s usually address book data, browsing history, files, etc.), as well as claim to have a video of you watching pornography.
In one of the emails we have encountered, scammers claim to have initially wanted to take the device for ransom, but changed their minds when they saw what kind of websites were being visited regularly. They’re, of course, talking about pornography. It’s a highly sensitive subject, and those who consume such content certainly do not want everyone to know exactly what kind of videos they enjoy. And not only do these scammers claim to know what videos are being watched, they also threaten the user with a video/screenshot of him/her watching such videos. If the user does not want that video to be sent to all contacts, he/she needs to send money in Bitcoin to the provided wallet address. Finally, the scammer then goes on to threaten the user to not remove the virus with security tools or attempt anything else.
Here’s a sextortion email example:
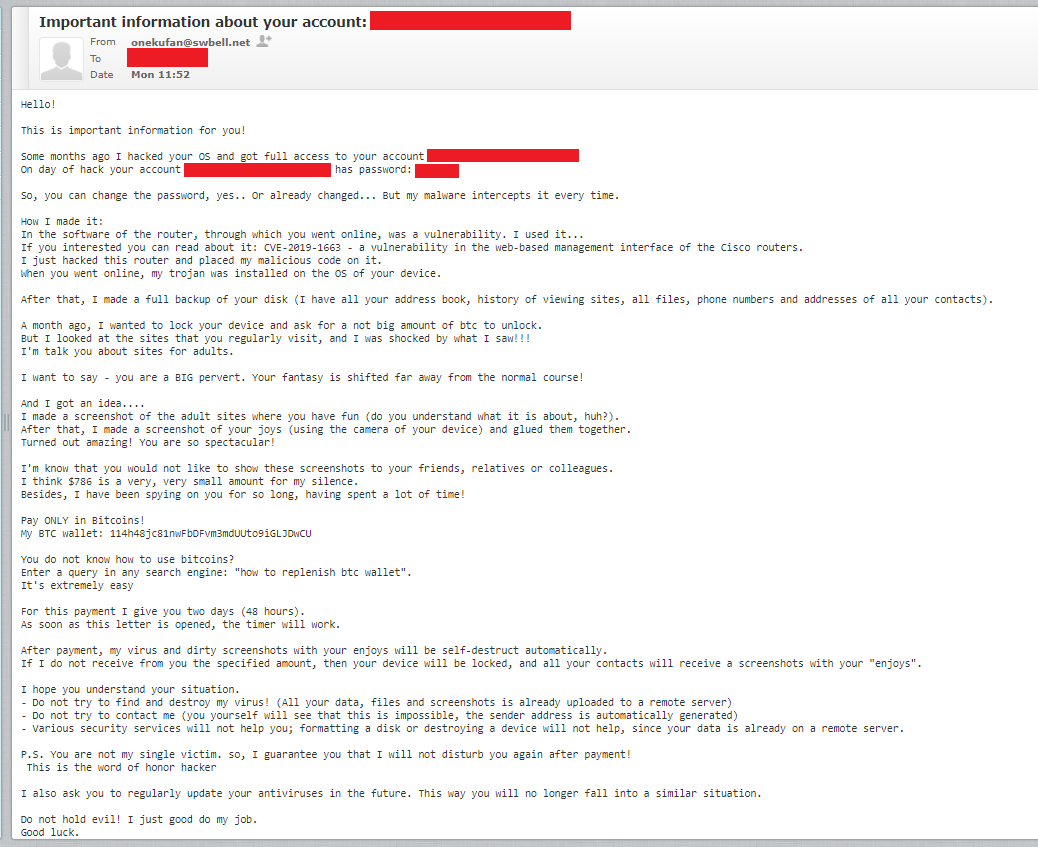
Hello!
This is important information for you!
Some months ago I hacked your OS and got full access to your account xxxx
On day of hack your account xxxxxx has password: xxxxx
So, you can change the password, yes.. Or already changed… But my malware intercepts it every time.
How I made it:
In the software of the router, through which you went online, was a vulnerability. I used it…
If you interested you can read about it: CVE-2019-1663 – a vulnerability in the web-based management interface of the Cisco routers.
I just hacked this router and placed my malicious code on it.
When you went online, my trojan was installed on the OS of your device.
After that, I made a full backup of your disk (I have all your address book, history of viewing sites, all files, phone numbers and addresses of all your contacts).
A month ago, I wanted to lock your device and ask for a not big amount of btc to unlock.
But I looked at the sites that you regularly visit, and I was shocked by what I saw!!!
I’m talk you about sites for adults.
I want to say – you are a BIG pervert. Your fantasy is shifted far away from the normal course!
And I got an idea….
I made a screenshot of the adult sites where you have fun (do you understand what it is about, huh?).
After that, I made a screenshot of your joys (using the camera of your device) and glued them together.
Turned out amazing! You are so spectacular!
I’m know that you would not like to show these screenshots to your friends, relatives or colleagues.
I think $786 is a very, very small amount for my silence.
Besides, I have been spying on you for so long, having spent a lot of time!
Pay ONLY in Bitcoins!
My BTC wallet: 114h48jc81nwFbDFvm3mdUUto9iGLJDwCU
You do not know how to use bitcoins?
Enter a query in any search engine: “how to replenish btc wallet”.
It’s extremely easy
For this payment I give you two days (48 hours).
As soon as this letter is opened, the timer will work.
After payment, my virus and dirty screenshots with your enjoys will be self-destruct automatically.
If I do not receive from you the specified amount, then your device will be locked, and all your contacts will receive a screenshots with your “enjoys”.
I hope you understand your situation.
– Do not try to find and destroy my virus! (All your data, files and screenshots is already uploaded to a remote server)
– Do not try to contact me (you yourself will see that this is impossible, the sender address is automatically generated)
– Various security services will not help you; formatting a disk or destroying a device will not help, since your data is already on a remote server.
P.S. You are not my single victim. so, I guarantee you that I will not disturb you again after payment!
This is the word of honor hacker
I also ask you to regularly update your antiviruses in the future. This way you will no longer fall into a similar situation.
Do not hold evil! I just good do my job.
Good luck.
In case it hasn’t been made clear, these emails are scams. Your computer is not infected with malware, scammers haven’t stolen your data, and they certainly do not have a video of you watching pornography. This is a sextortion attempt that you should pay no attention to.
How do sextortion scammers obtain your email addresses and passwords
Now that it’s clear that these sextortion emails are simply scams, we should explain how scammers manage to get information like passwords, account names, and phone numbers. It’s pretty simple actually, such data is acquired from old data dumps. If you had an account on a website that was hacked at some point, your information likely became part of a data package sold on the Internet. Scammers buy those data packages and proceed to send sextortion emails to all email addresses that come in the package. This is why the password in the sextortion email you received is unlikely to be one you currently use, unless you have bad security habits and do not change your passwords regularly.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
