How to remove Trial_recovery ransomware
Trial_recovery ransomware is malware that encrypts files. It’s a severe infection that can result in permanently lost files. The ransomware can be identified by the .trial-recovery.[random characters].[random characters].-encrypted extension added to all encrypted file names. If you have a backup of your files, you can start file recovery as soon as you remove Trial_recovery ransomware from your computer. However, users without backups are unlikely to get their files back.
When users open the infected file and the malware is initiated, it will immediately begin encrypting files. Unfortunately, the ransomware’s main targets are personal files, which users hold most important, including documents, photos, videos, images, etc. Encrypted files will be immediately recognizable because of the extensions added to encrypted file names. This ransomware adds the following extension to encrypted files: trial-recovery.[random characters].[random characters].-encrypted. For example, an encrypted text.txt file would become text.txt.trial-recovery.[random characters].[random characters].-encrypted.
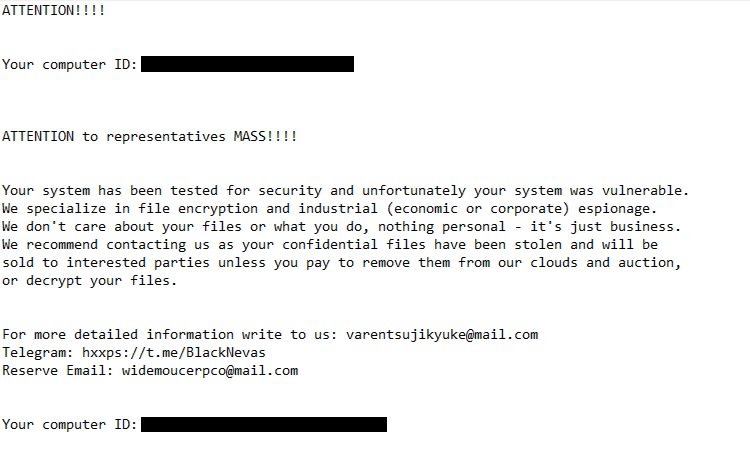
The ransomware drops how_to_decrypt.txt ransom note. The note explains that the victim’s system was vulnerable, which led to its infection. The note also mentions that files have not only been encrypted but also stolen. Unless victims agree to pay the ransom, cybercriminals threaten to auction the data to interested parties. Whether victims pay the ransom is their decision but it’s never recommended.
The full Trial_recovery ransomware ransom note is below:
ATTENTION!!!!
Your computer ID:
ATTENTION to representatives MASS!!!!
Your system has been tested for security and unfortunately your system was vulnerable.
We specialize in file encryption and industrial (economic or corporate) espionage.
We don’t care about your files or what you do, nothing personal – it’s just business.
We recommend contacting us as your confidential files have been stolen and will be
sold to interested parties unless you pay to remove them from our clouds and auction,
or decrypt your files.For more detailed information write to us: varentsujikyuke@mail.com
Telegram: hxxps://t.me/BlackNevas
Reserve Email: widemoucerpco@mail.comYour computer ID:
If you have a backup, you can connect to it and start file recovery as soon as you remove Trial_recovery ransomware from your computer. We strongly recommend using an anti-malware program to delete Trial_recovery ransomware because it’s a complex malware infection. Once the ransomware is no longer detected, it’s safe to connect to your backup.
Unfortunately, there currently is no free Trial_recovery ransomware decryptor available. Thus, if users have no backup and are not planning on paying the ransom, they will not be able to recover files at this moment.
How is ransomware distributed?
Several methods are used to distribute ransomware, including torrents, email attachments, malicious links/ads, etc. Users who have bad browsing habits are considerably more likely to pick up an infection because they engage in risky online behavior more often. Developing healthier online habits is a good way to avoid malware infections. We also recommend you become familiar with common malware distribution methods.
Emails are a common way malware is distributed. Emails carrying malware are often disguised to resemble parcel delivery notifications or order confirmations. As a way to attract users’ attention, malicious emails often mention large sums of money and supposed expensive purchases. Because this creates a sense of urgency for users, it’s quite an effective tactic. However, if users take a closer look at these emails, they should be easily identifiable as malicious. Firstly, malicious emails generally have very obvious grammar/spelling mistakes. Legitimate emails will never have such glaring mistakes because they look very unprofessional. Another sign is malicious emails addressing recipients with generic words like User, Member, Customer, etc. When corresponding with customers, legitimate companies address users by names, or rather by the names users have given the companies. However, malicious actors rarely have extensive access to personal information besides email addresses so they are forced to use generic words.
You should also be aware that when malicious emails have specific targets, they are much more sophisticated. The emails would not have any of the obvious signs of a malicious email, address the target by name, and contain information that gives the email at least some credibility. Thus, we always recommend you avoid opening unsolicited email attachments before first scanning them with anti-virus software or VirusTotal.
Torrents are another common way for malware to be distributed. It’s not a secret that torrent sites can be dangerous due to their poor moderation. This allows malicious actors to upload torrents with malware in them. Entertainment content (e.g. movies, TV series, video games, etc.) torrents in particular often have malware in them. If you regularly pirate copyrighted content, you’re not only stealing content but also putting your computer and data in danger.
How to remove Trial_recovery ransomware
Ransomware is a very serious malware infection, which is why using an anti-virus program is a good idea. Unless you know exactly what you’re doing, trying to manually remove Trial_recovery ransomware could cause additional damage to your computer. If you have a backup of your files, you can connect to it and start recovering files as soon as you remove Trial_recovery ransomware from your computer. Keep in mind that if your computer is still infected with ransomware when you connect to your backup, the backed-up files will become encrypted as well.
If you do not have a backup, your only option is to wait for a free Trial_recovery ransomware decryptor to be released. However, whether a free decryptor will be released is not certain because these infections are difficult to crack for specialists. If it does get released, it will become available for download on NoMoreRansom.
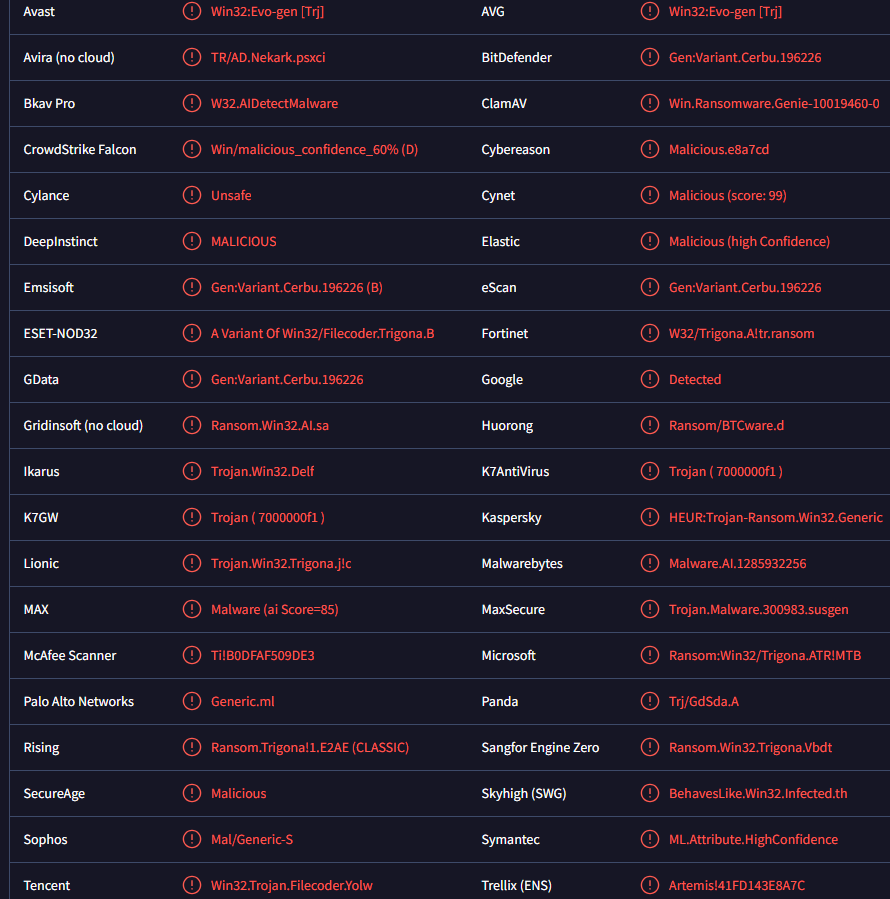
Trial_recovery ransomware is also detected as:
- Win32:Evo-gen [Trj] by AVG/Avast
- A Variant Of Win32/Filecoder.Trigona.B by ESET
- HEUR:Trojan-Ransom.Win32.Generic by Kaspersky
- Malware.AI.1285932256 by Malwarebytes
- Ransom:Win32/Trigona.ATR!MTB by Microsoft
- Ransom_Trigona.R002C0DI624 by TrendMicro
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.