How to remove Payfast ransomware
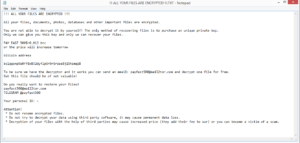
Payfast ransomware encrypts personal files and demands a ransom payment in exchange for a decryptor. It’s a fairly typical ransomware infection and is a new ZEPPELIN ransomware variant. You can identify this ransomware by the extension added to encrypted files. It adds .payfast followed by the ID assigned to you. Once file encryption is done, “!!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT” ransom note will be dropped. Currently, free file decryption is not possible.
As soon as the ransomware is initiated, it will start encrypting files. In terms of the files it targets, it’s fairly standard. It will encrypt photos, videos, images, and documents. It’s impossible to not notice that files have been encrypted because you will not be able to open them and they will have .payfast followed by your assigned ID attached to them. For example, image.jpg would become image.jpg.payfast[assigned ID]. Once all files have been encrypted, the ransomware will drop a “!!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT” ransom note. The note explains that files have been encrypted and that purchasing the private key is the only way to decrypt them. That is, unfortunately, correct as there is no free decryptor at this time. The cyber crooks operating this ransomware are asking for $500 in Bitcoin to be sent to the provided wallet address. While paying might seem like a good option we recommend against doing that. While the decision of whether to pay is yours, you should be aware of the risks involved. First of all, there are no guarantees that you will actually get the decrytpor considering that there is nothing obligating them to send it to you. They can easily take the money, as countless cybercriminals have done in the past. Furthermore, if you pay, you will become a likely target again in the future as the crooks know you’re willing to pay. Finally, it should be mentioned that as long as victims pay the ransom, ransomware will continue to be an issue.
If you have a backup, file recovery shouldn’t be an issue. However, be warned that if the ransomware is still present when you access your backup, backed-up files would become encrypted as well. Thus, use anti-virus software to remove Payfast ransomware and only then access your backup to start recovering files.
Recovering files will be tricky for those who do not have a backup as a free decryptor is not currently available. It’s not impossible that it will be released sometime in the future so you should back up encrypted files and wait. However, you should be very careful about downloading decryptors because there are many questionable sources, and you may end up downloading malware instead of a decryptor. NoMoreRansom is a reliable source for decryptors so you should check that.
How does ransomware infect a computer?
This ransomware uses the typical distribution methods, thus users with good browsing habits have a much lower chance of picking it up, or any malware in general. Typically, malware is distributed through spam email attachments, torrents, malicious ads/updates/downloads, rootkits, etc. If you take the time to develop better browsing habits, you will avoid a lot of malware in the future.
You likely already know this but torrents are one of the most common ways users pick up malware infections. The majority of torrent sites are notorious for being badly moderated, allowing anyone to upload anything, including malware. It’s particularly common to find malware in torrents for popular entertainment content, such as movies, TV series, video games, and software. So if you are an avid torrent user, you are not only essentially stealing content but also putting your computer in danger.
Another common way malware is distributed is via malicious spam emails. Email addresses to which malspam is sent are usually purchased from various hacker forums so if your email address has ever been leaked or part of a data breach, you may receive malicious emails on a regular basis. These emails are written to resemble official correspondence from various companies or government organizations and put strong pressure on users to open the attachments. They also deliberately use an intimidating tone in order to scare users. And once the attached file is opened, the malware is initiated. Fortunately for users, unless crooks target someone specific, they will put in very little effort into these emails which makes it quite easy to recognize it. It’s impossible to not notice the abundance of grammar and spelling mistakes, awkward English, and the weird tone of the email. Furthermore, the emails refer to users as Users, Customers, Members, etc., while claiming to be companies whose services users use. Legitimate companies use customers’ names when sending them official correspondence, thus generic greetings should raise alarms bells. But because some emails may be more sophisticated than others, it’s a good idea to scan all unsolicited email attachments with anti-virus software or VirusTotal before opening them.
Finally, avoid clicking on advertisements and other questionable content when browsing websites that are considered to be high-risk. Even clicking on a seemingly harmless advertisement could lead you to a website trying to trick you into downloading malware. It’s highly recommended to have anti-virus software installed and adblocker enabled when browsing such sites.
Payfast ransomware removal
When it comes to ransomware, manual removal is rarely recommended because of how complicated the infection is. We strongly recommend you use anti-virus software to delete Payfast ransomware from your computer because you could end up causing additional damage otherwise. Once the ransomware is no longer present, you can start recovering files from your backup. However, be careful to make sure the ransomware is fully gone before accessing your backup because those files would become encrypted as well.
For those without backup, file recovery options are very limited. It’s not impossible that a free decryptor will be released sometime in the future so users should back up the encrypted files and check NoMoreRansom every now and then for a free decryptor. It’s also highly recommended to regularly back up any important files in order to avoid possible file loss in the future.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.