How to remove Paaa ransomware
Paaa ransomware is a type of malware that encrypts personal files. It essentially keeps files hostage until users agree to pay a ransom. Once files have been encrypted, it will not necessarily be possible to get them back. Only users who have backups can currently decrypt files for free.
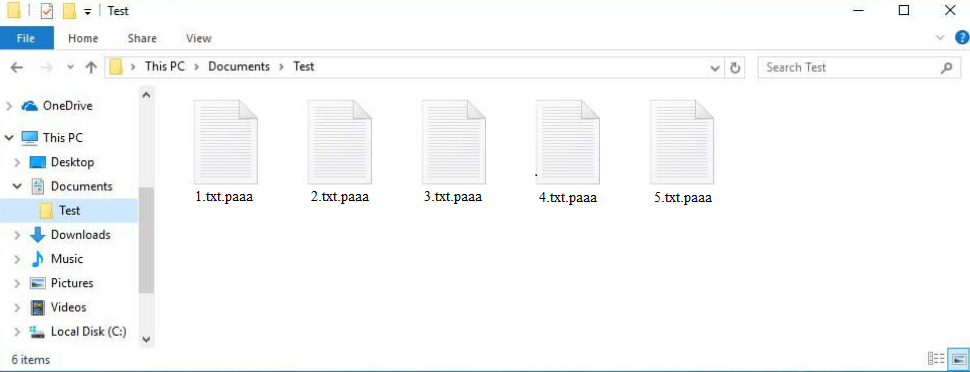
Paaa ransomware is part of the Djvu/STOP ransomware family. All Djvu versions are more or less the same, and they can be recognized by the extensions they add to encrypted file titles. This ransomware adds .paaa, hence why it’s known as Paaa ransomware. If the ransomware is on your computer, all your personal files will have this extension, including photos, videos, images, and documents. For example, 1.txt would become 1.txt.paaa if encrypted. You cannot open files with this extension unless you first run them through a decryption program.
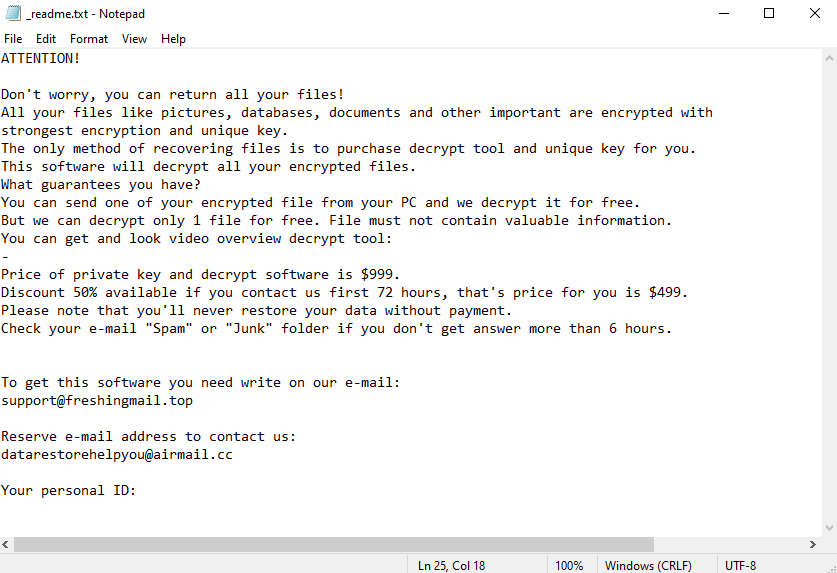
The ransomware operators explain how to get the decryption program in the _readme.txt ransom note that’s dropped once files are encrypted. According to the note, the decryption tool costs $999 but there’s a 50% discount for victims who make contact within the first 72 hours. The malware operators also promise to decrypt one file for free if it contains no important information. It’s supposed to be proof that they have a working decryptor.
Here is the full _readme.txt ransom note:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
Do not ask assistants from youtube and recovery data sites for help in recovering your data.
They can use your free decryption quota and scam you.
Our contact is emails in this text document only.
You can get and look video overview decrypt tool:
–
Price of private key and decrypt software is $999.
Discount 50% available if you contact us first 72 hours, that’s price for you is $499.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshingmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
Paying the ransom is never a good idea for several reasons. One of the biggest reasons has to do with the fact that the malware operators are cybercriminals. They are unlikely to feel any obligation to help victims and there’s nothing to force them to send the decryptor. Unfortunately, many victims have paid the requested ransom but received nothing in return. We should also mention that the money victims pay goes towards future criminal activities. Whether you pay the ransom or not is your choice but you need to be aware of the risks.
If you have a backup, you can start file recovery as soon as you remove Paaa ransomware from your computer. Ransomware is a complex infection so you need to use a good anti-malware programs to delete Paaa ransomware. When the anti-virus program no longer detects the ransomware, you can safely connect to your backup and start recovering files. If you do not have a backup, you have limited file recovery options. We recommend backing up the encrypted files and storing them separately until a free Paaa ransomware decryptor is released. NoMoreRansom is a great source for decryptors. If you cannot find a Paaa ransomware decryptor on NoMoreRansom, you likely won’t find it anywhere else.
How is Paaa ransomware distributed?
Malware operators use the usual methods to distribute the ransomware, including torrents, email attachments, malicious links/ads, etc. If users have poor browsing habits, they are much more likely to pick up an infection. Thus, developing better habits is a great way to avoid future malware infections, as is becoming familiar with common malware distribution methods.
Emails are an easy malware distribution method, one commonly used to spread ransomware. Emails carrying malware are often disguised as parcel delivery notifications and order confirmations. They also often mention large sums of money and claim that the attached files are important documents that need to be reviewed immediately. This is an effective tactic because it creates a sense of rush that pressures users to react. But what gives these emails away as malicious is the grammar/spelling mistakes. The mistakes are usually very obvious. You will never see such mistakes in legitimate emails so it’s obvious when an email is spam/malicious.
Generic words like User, Member, Customer, etc., being used to address you by a sender who should know your name can be another sign of a potentially malicious email. In an effort to make the email seem more personal, legitimate emails use users’ names when addressing them. However, malicious emails use generic words to address users because they do not have access to personal information other than an email address. They also target many users with the same email.
Malicious emails are significantly more sophisticated when the operators have a specific target in mind. Such emails would contain a lot of the target’s personal information to make the emails more credible. To avoid opening something malicious, it’s important to scan all unsolicited email attachments with anti-virus software or VirusTotal before opening them.
Torrents are another common malware distribution method. Torrent sites are often poorly moderated, which allows malicious actors to upload torrents with malware in them. It’s especially common to find malware in torrents for entertainment content (e.g. movies, TV series, video games, etc.). If you torrent, you’re not only stealing content but also putting your computer and data in danger.
Paaa ransomware removal
When it comes to complex malware infections like ransomware, it’s best to use a good anti-malware program. Do not attempt to remove Paaa ransomware manually because you could end up causing additional damage to your computer. When the ransomware is no longer present, you can connect to your backup and start recovering files. If backup is not an option, back up the encrypted files and wait for a free Paaa ransomware decryptor to be released.
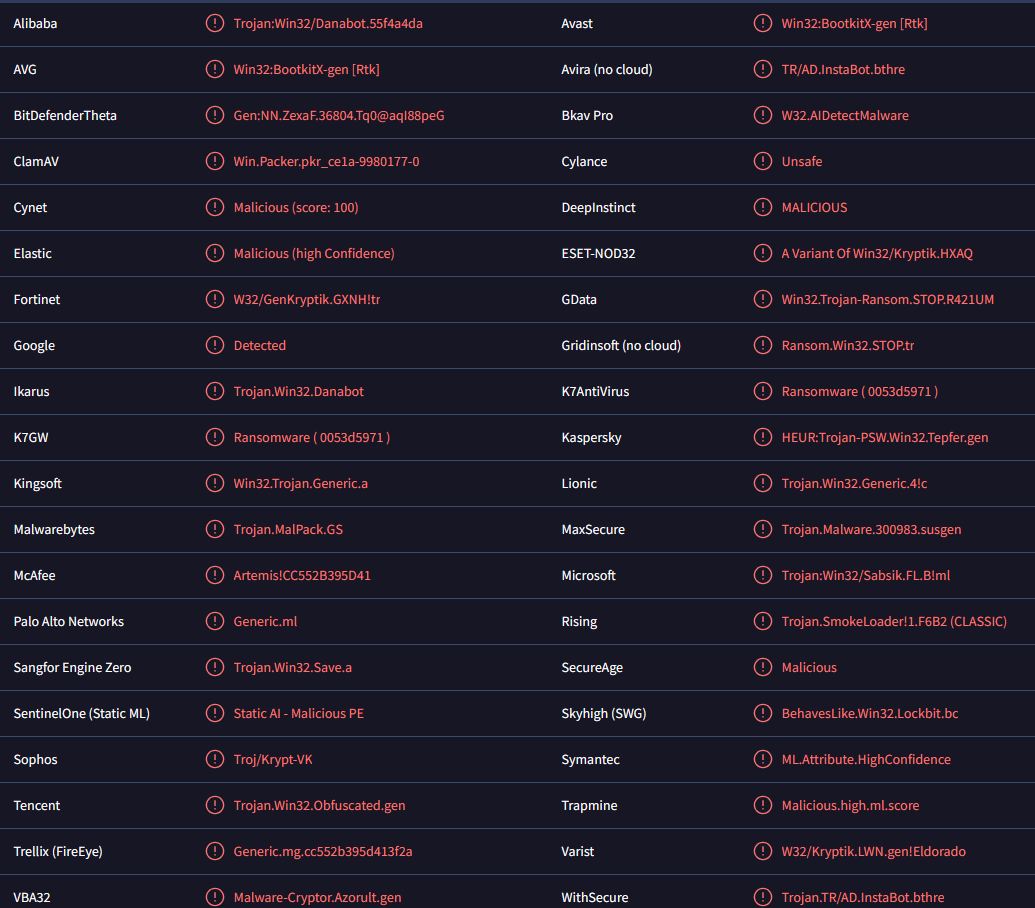
Paaa ransomware is also detected as:
- Win32:BootkitX-gen [Rtk] by Avast/AVG
- Trojan.GenericKD.72741121 by BitDefender
- A Variant Of Win32/Kryptik.HXAQ by ESET
- HEUR:Trojan-PSW.Win32.Tepfer.gen by Kaspersky
- Artemis!CC552B395D41 by McAfee
- ML.Attribute.HighConfidence by Symantec
- Trojan.MalPack.GS by Malwarebytes
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.