How to Identify and Protect Yourself from Tech Support Scams
Tech support scammers falsely claim that there is something wrong with your computer so they can trick you into paying for tech support services you do not actually need. Tech support scams are a huge issue that costs millions of dollars to consumers every year. While not very sophisticated, these scams take advantage of users who know little about computers. Thus, scammers can trick victims into paying hundreds of dollars.
According to the US Federal Trade Commission, consumers have lost $148 million to gift card scams in the first nine months of 2021. A large portion of those gift card scams is tech support scams that use gift cards to steal victims’ money. Gift cards are the preferred method of payment for tech support scammers because it allows them to remain relatively anonymous and transactions are mostly irreversible.
There are thousands of tech support scams but they all follow a very similar pattern. To the point that once you’ve seen one, you’ve seen most of them. Thus, for users who know what a tech support scam looks like, they’re fairly easy to recognize. However, the targets of such scams are not tech-savvy people. Rather, scammers mostly engage with the elderly who know very little about computers.
How do tech support scams work
Tech support scammers target victims via phone calls, pop-ups, emails, text messages, etc. Some targets are completely random, while others are intentional. They start off with scammers making contact with victims in some way. For example, a victim may receive a robot voice call with a message saying that there is something wrong with their computers and they need to call a certain number. Or victims may come across a pop-up alert with a phone number that claims a virus has been found on their computer. However the scammers make contact, they ask that users call a certain number to receive technical support.
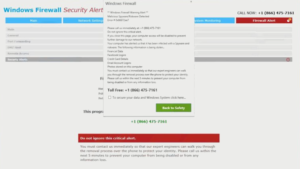 An example of a tech support scam pop-up
An example of a tech support scam pop-up
If users call the number, they are connected to professional scammers who pretend to be technicians working for companies like Microsoft or Apple. They first ask why users are calling, and when users read the message they received, scammers begin their scam. They make the supposed issue sound very serious, usually by claiming that the malicious infection on the computer is stealing personal information and files. To supposedly remove the malware, scammers request that users give them remote access to their computers. They guide users into downloading software that would allow the supposed technicians to remotely access users’ computers. Once they have remote access, they display fake proof of a malicious threat’s presence and then pretend to remove it. While the scammers are “cleaning” computers of malware, they may also steal files, financial information, or set a password for the computer. This can last up to a couple of hours, depending on the scammer.
When scammers go through the script they have for the scam, they will ask that users pay for the repair services they have received. They usually demand at least a couple of hundred dollars. Some users may hesitate to pay. But scammers are prepared for that. While remotely connected to the computer, scammers may lock the computer and set a password only they know. Unless the victim agrees to pay, they would not be able to access their device and files.
If you are interested in what a tech support scam looks like in real life, you can find many videos on YouTube of people purposely engaging with tech support scammers to waste their time and prevent them from actually scamming someone.
If users agree to pay, they are usually instructed to purchase gift cards. Generally, to prevent victims from contacting someone who would be able to reveal the scam, scammers stay on the phone with the victim while he/she buys the gift cards. They even coach victims on what to say at the register because most store employees are aware of these scams and may warn victims if they notice anything suspicious. Once victims purchase the gift cards, scammers ask for the numbers on the card so they can redeem the money.
If tech support scammers successfully scam a victim, they will likely contact him/her again in the future with a similar scam.
How to protect against tech support scams
As we mentioned already, tech support scams are fairly obvious if you know what to look for. Here are a few things to keep in mind that can help recognize tech support scams:
- Neither Microsoft nor Apple make unsolicited contact with users, whether it’s to fix a computer or request personal information. All communication has to be initiated by the user.
- Legitimate alerts about malware’s presence on a computer will come only from the installed anti-virus program, never the browser. Browsers are unable to detect viruses or other issues on a computer.
- No legitimate alert about issues on a computer will have a phone number for tech support. The presence of a phone number is an immediate giveaway that it’s a scam.
- Legitimate companies like Microsoft or Apple do not ask for payments using cryptocurrencies or gift cards.
And here are a few tips to avoid tech support scams:
- Use anti-virus software to protect your computer. There are plenty of very trustworthy anti-virus programs available, it’s only a matter of choice.
- Install an adblocker. The tech support scam alerts that appear in browsers are pop-up ads. If you install an adblocker program, it should be able to block them from even appearing on your screen.
- Change browser settings to block pop-ups. All popular browsers now have this setting so there should be no trouble with you changing it.
- Never allow unknown parties remote access to your computer.
- If you need to call technical support, double-check that the phone number is legitimate before calling. Scammers use various techniques to push their fake tech support numbers and can even make them appear in a Google search among the top results. For example, if you need Microsoft’s tech support, navigate its official website to find ways to contact technicians.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.

