Eking ransomware removal
Eking ransomware is file-encrypting malware. This is just another version of the Phobos ransomware family. It’s classified as a very serious malware infection because once on the computer, it proceeds to encrypt all personal files. None of the encrypted files will be openable unless you first use a decryptor on them. However, acquiring the decryptor is not going to be easy because the only people who have it are the cyber criminals operating this ransomware. More details about this ransomware can be found below.
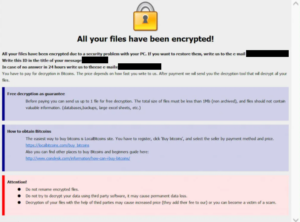
Eking ransomware comes from the notorious Phobos ransomware family. The cybercriminals operating these ransomware versions release new malware on a regular basis, infecting thousands of users. This ransomware targets personal files and that includes photos, videos, images, documents, etc. These files are usually the primary targets because users are most often willing to pay for them. This ransomware renames all encrypted files making it difficult to know which file is what. For example, an encrypted text.txt file would become 1.txt.id[unique ID].[decphob@tuta.io].eking. The IDs are unique to each victim, and yours would need to be included if you were to contact the cybercriminals for a decryptor. How you can acquire the decryptor will be explained in the ransom notes.
Eking ransomware has two ransom notes, one pop-up and one text note. Both notes explain how to acquire the decryptor. Unfortunately, you’d have to buy it from the cybercriminals operating this ransomware. The price for the decryptor is not mentioned in the note and would likely be revealed if you were to contact them using the email addresses provided in the ransom notes. The notice offer to decrypt five files for free provided they do not contain any personal information. That’s supposed to prove to victims that cybercriminals can decrypted files. Unfortunately, paying the ransom comes with many risk which is why it’s not recommended to engage with the cybercriminals. Keep in mind that there they are not obligated to help you and they’re unlikely to feel like they should. Paying is your decision but you do need to be aware of the risks. Furthermore, the reason why ransomware is still such a big issue is because victims keep paying the ransom.
There currently is no free Eking ransomware decryptor available. That may change in the future, which is why you should back up your encrypted files and occasionally check reliable sources for a free decryptor. If you do have a backup, you can start the file recovery process as soon as you remove Eking ransomware from your computer. Make sure to use an anti-malware program because manual Eking ransomware removal is not safe.
Ransomware distribution methods
Cybercriminals distribute ransomware threats like Eking ransomware in a variety of ways. Including email attachments, ads on high-risk websites, torrents, etc. Usually, users with good online habits are much less likely to pick up malware infections. So if you take the time to develop better browsing habits, you will be able to avoid a lot of malware infections in the future.
Malicious actors often use email attachments to distribute malware. It’s very low effort method because all criminals need to do is purchase email addresses from various hacker forums and then spam those addresses with malicious emails. Fortunately for users, these emails are harmless as long as users do not interact with them. However, if users open the attached malicious files, the malware would be authorized to initiate. The emails are, fortunately, very easy to recognise. They are full of grammar and spelling mistakes which is something that you should immediately notice. No legitimate email will ever contain obvious grammar or spelling mistakes because it would look unprofessional. Furthermore, malicious emails usually address users with generic words like User, Member, Customer, etc. When a company whose services you use sends you an email asking you to open an attachment, the email will always address you by your name because the name is put in automatically. However, there are cases where the emails may be much more sophisticated. This is why it’s a good idea to always can email attachment with an anti-malware program or VirusTotal.
If you pirate copyrighted content using torrents, you are putting your computer and your data in danger. Oftentimes, torrent websites are poorly regulated which allows malicious actors to easily upload malicious content. Malware is often found in torrents for popular movies, TV series, video games, software, etc.
Eking ransomware removal
It’s necessary to use anti-malware software to remove Eking ransomware from your computer. Do not attempt to delete Eking ransomware manually by yourself unless you know exactly what to do. If you’re not careful, you could end up causing additional damage. Once the ransomware has been fully removed, you can access your backup and start recovering files. If you do not have a backup, back up the encrypted files and wait for a free decryptor to be released. NoMoreRansom is a good source for decryptors.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.