Cybersecurity news headlines for May 2022
May’s edition of cybersecurity news headlines covers 4 interesting stories. One of the biggest stories in May was hackers successfully defacing Russia’s TV schedule page to display anti-war messages, as well as temporarily taking down RuTube, a Russian video content provider. In other news, Twitter has been fined $150 million for using users’ 2FA personal information for targeted advertising, a Lianjia employee has been sentenced to 7 years in prison for purposely wiping the company’s database, and the US Department of Justice will no longer prosecute ethical hackers.
Without further ado, here are the most interesting cybersecurity stories to hit the news in May 2022.
Hackers successfully hijack Russia’s TV schedule page to display anti-war messages
After Russian military forces began the invasion of Ukraine on February 24 this year, hackers from all over the world have started targeting Russia with cyberattacks. In one of the most recent attacks, hackers were able to deface the online Russian TV schedule page to display anti-war messages. They were also able to take down the RuTube video streaming site. The attack occurred during Russian President Putin’s speech at the controversial “Victory Day” military parade on May 9.
Those in Russia attempting to access TV schedules on their smart TVs were met with messages accusing the Kremlin of propaganda and that the blood of thousands of killed Ukrainians was on their hands. The anti-war message was further spread by search engines that index TV schedules.
“On your hands is the blood of thousands of Ukrainians and their hundreds of murdered children. TV and the authorities are lying. No to war,” the messages read.
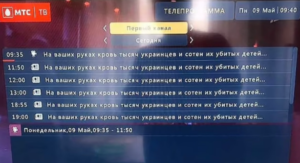 TV schedule page displaying anti-war messages
TV schedule page displaying anti-war messages
Russian video content provider RuTube also suffered a cyberattack. RuTube provides similar services to YouTube but mostly caters to Russian-speaking users. For a period of time, users entering the site were greeted with a message saying the site was undergoing technical work. According to the company’s posts on Telegram, the hackers were not able to access video archives.
“Following the websites of Russian departments, which have been constantly subjected to cyberattacks over the past two months, hackers have reached RUTUBE. Video hosting has undergone a powerful cyberattack. At the moment it is not possible to access the platform,” RuTube said in a Telegram message.
No hacker group has taken responsibility for the attack.
An employee who wiped the entire employer’s database has been sentenced to 7 years in prison
An employee of the Chinese real-estate brokerage giant Lianjia has been sentenced to 7 years in prison after it became clear that he logged into corporate systems and deleted the company’s data. The incident occurred in June 2018 when then database administrator, identified as Han Bing, used his administrative privileges to access the company’s financial system. He proceeded to delete all stored data from two database servers and two application servers.
Lianjia, previously known as Homelink, is a massive real-estate brokerage company that employs over 120,000 brokers and has a market value of $6 billion. Completely wiping the four servers immediately crippled the majority of the company’s operations. As a result, tens of thousands of Lianjia employees were unable to receive their salaries for the time it took the company to resolve the issue. It is estimated that restoration efforts have cost the company at least $30,000.
It was not immediately clear who was responsible for the incident but the suspect list was narrowed to only five employees who had the necessary clearance to access the data. According to reports, Han initially declined to give his laptop password to the company’s investigators, which immediately raised suspicion. Han claimed that his laptop contained personal data, and agreed to only provide his password if he himself was present during checks. Han’s reaction raised suspicion because he was the only one of the five suspects to initially refuse the request. While no traces were left on the laptop, investigators retrieved access logs from the servers and were able to trace the activity to specific internal IPs and MAC addresses. They were also able to retrieve WiFi connectivity logs/timestamps and correlated them with CCTV footage. Han Bing then became the official suspect.
It is not completely clear why Han did what he did, though he allegedly was not satisfied with the company’s response to his reports about security gaps in the system.
The US DOJ will no longer prosecute ethical hackers
The US Department of Justice has announced that ethical hackers will no longer be prosecuted under the Computer Fraud and Abuse Act (CFAA). Following this revision of the policy, the DOJ will separate malicious hacking from ethical hacking. The DOJ recognizes that software testing, vulnerability analyses, breaches, investigation, etc., intended to promote security should not be prosecuted.
“The policy for the first time directs that good-faith security research should not be charged. Good faith security research means accessing a computer solely for purposes of good-faith testing, investigation, and/or correction of a security flaw or vulnerability, where such activity is carried out in a manner designed to avoid any harm to individuals or the public, and where the information derived from the activity is used primarily to promote the security or safety of the class of devices, machines, or online services to which the accessed computer belongs, or those who use such devices, machines, or online services,” the DOJ’s statement reads.
The DOJ’s statement goes on to explain that the department has never been interested in prosecuting ethical hacking as a crime. The new policy will allow the department to focus its resources on cases where the hacker does not have the authorization to access a device or is authorized to access only one part, and despite these restrictions still accessed the device or part of it. Claiming to be conducting security research does not apply to those acting in bad faith. Using identified device vulnerabilities in order to extort device owners is still malicious acting, even if the “research” defense is used.
Despite the amendment to the policy, whether ethical hackers get charged is still decided by federal prosecutors. Therefore, it’s still safest for white hat hackers to join bug bounty programs or at least research a company’s vulnerability research guidelines.
Twitter fined $150 million for using 2FA phone numbers for targeted advertising
The US Federal Trade Commission (FTC) has issued Twitter a fine of $150 million for using two-factor authentication phone numbers and email addresses for targeted advertising. Twitter encourages users to secure their accounts with two-factor authentication (2FA) regularly but failed to inform its users that their provided means of 2FA (e.g. phone number) would be shared with advertisers for advertising purposes. This is believed to have affected more than 140 million Twitter users. This is a violation of the 2011 FTC order that prohibits the company from misrepresenting its privacy and security practices. As a result, Twitter must now pay a $150 million fine and has been banned from profiting from its deceptively collected data.
“In a complaint filed today in the U.S. District Court for the Northern District of California, the government alleges that Twitter violated the FTC Act and the 2011 order by deceiving users about the extent to which Twitter maintained and protected the security and privacy of users’ nonpublic contact information. Specifically, the complaint alleges that, from May 2013 to September 2019, Twitter told its users that it was collecting their telephone numbers and email addresses for account-security purposes, but failed to disclose that it also would use that information to help companies send targeted advertisements to consumers,” a notice by the Department of Justice reads.
More than 140 million Twitter users provided their phone numbers from 2014 to 2019 after Twitter prompted them to secure their accounts with 2FA. However, the social media giant failed to mention that the provided email addresses and phone numbers would be used to allow advertisers to target users with customized ads. Advertisers matched the email addresses and phone numbers to data they already had, which allowed them to target these users with custom ads.
Twitter has agreed to pay the $150 million fine and will implement new measures to improve its data privacy practices. Twitter is also obligated to inform US Twitter users who joined before September 17, 2019, about this settlement and to provide them with options for protecting their privacy and security. New measures include:
- Developing and maintaining a comprehensive privacy and information-security program;
- Conducting a privacy review with regular testing of its data privacy safeguards;
- Regular assessments of its data privacy program from an independent assessor;
- Annual certifications of compliance from a senior officer;
- Providing reports after any data privacy incidents that affect 250 or more users;
- Complying with other reporting and record-keeping requirements.
References
- Mia Jankowicz. Hackers replaced Russian TV schedules during Putin’s ‘Victory Day’ parade with an anti-war message saying the blood of Ukrainians is on Russians’ hands. Business Insider.
- Department of Justice Announces New Policy for Charging Cases under the Computer Fraud and Abuse Act. The US Department of Justice.
- FTC Charges Twitter with Deceptively Using Account Security Data to Sell Targeted Ads. Federal Trade Commission.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.

