Cybersecurity news headlines for January 2021
In January’s edition of news headlines, we report on some of the biggest cybersecurity stories that happened in January, 2021. More details emerged on the SolarWinds hack, including who may be responsible, two large-scale law enforcement operations have taken down illegal DarkMarket marketplace and Emotet malware, and Internet’s biggest credit card forum Joker’s Stash announced it’s shutting down.
Without further ado, here’s what made the biggest cybersecurity headlines in January 2021.
The SolarWinds hack and the fallout
In last month’s edition of cybersecurity news headlines, we reported on the massive SolarWinds attack that was revealed in December 2020. During the attack, malicious actors were able to get into SolarWind’s systems and add malicious code into Orion, SolarWind’s IT resource management software used by 33,000 companies. Orion updates, released between March and June 2020, contained the malicious code. Ultimately, 18,000 Orion customers installed the updates, though only a small amount of them had any follow-up malicious activity. Among those affected was the Department of Homeland Security, the Department of Energy, the National Nuclear Security Administration, and the Treasury. It was later revealed that the US Department of Justice was also affected. Reportedly, attackers were able to access the Department of Justice Microsoft O365 email server.
In a joint statement released on January 5, 2021, the FBI (Federal Bureau of Investigation), CISA (the Cybersecurity and Infrastructure Security Agency), ODNI (the Office of the Director of National Intelligence), and NSA (National Security Agency) revealed that the attack was carried out by an Advanced Persistent Threat (APT) actor who was likely “Russian in origin”. Russia has denied any involvement in the hack.
The statement also announced a new task force Cyber Unified Coordination Group (UCG) made up of the above-mentioned agencies. The task force is responsible for coordinating the investigation into the SolarWinds hack.
 A statement released by the joint task force UCG (Cyber Unified Coordination Group
A statement released by the joint task force UCG (Cyber Unified Coordination Group
Cybersecurity company Malwarebytes later revealed that they were targeted by the same group of malicious actors behind SolarWinds. In a statement released on January 19, 2021, CEO of Malwarebytes Marcin Kleczynski said that attackers were able to get access to a limited subset of internal company emails. Malwarebytes confirmed that they do not use SolarWinds software, and revealed that there is another intrusion vector that was used by the malicious actors.
“While Malwarebytes does not use SolarWinds, we, like many other companies were recently targeted by the same threat actor. We can confirm the existence of another intrusion vector that works by abusing applications with privileged access to Microsoft Office 365 and Azure environments,” Kleczynski said.
Malwarebytes also said they found no evidence to suggest unauthorized access or compromise in their internal on-premises and production environments.
DarkMarket marketplace taken down during an international operation
World’s largest illegal marketplace DarkMarket has been taken offline after an international operation involving Germany, Australia, Denmark, Moldova, Ukraine, the United Kingdom, and the US, with Europol providing support.
DarkMarket is considered to be one of the largest illegal marketplaces, with over 500,000 users, more than 2,400 sellers, over 320,000 transactions, and more than 4,650 Bitcoin and 12,800 monero (around €140 million overall) transferred within the marketplace. The marketplace primarily traded drugs, counterfeit money, stolen credit card details, anonymous SIM cards and malware.
DarkMarket began its operation in 2019 and was founded by a man now known to be a 34-year old Australian citizen. He was arrested near the German-Danish border by the Central Criminal Investigation Department. The investigation, led by Koblenz Public Prosecutor’s Office’s cybercrime unit, resulted in officers being able to locate and close the marketplace, switch off the servers and seize the criminal infrastructure. Reportedly, more than 20 servers in Moldova and Ukraine were seized. The seized data will be used to track down moderators, sellers and buyers.
The Guardian reports that DarkMarket was first noticed by law enforcement during a large-scale investigation into web-hosting service Cyberbunker, which was known for hosting the torrent website The Pirate Bay and multiple WikiLeaks mirrors.
While law enforcement agencies have been cracking down on illegal marketplaces, sellers and buyers suffer little inconvenience as they can migrate to other operational dark web marketplaces.
Joker’s Stash marketplace announces shutdown
Internet’s largest marketplace for stolen cards Joker’s Stash has announced that it’s shutting down on February 15, 2021. The announcement comes after a rater turbulent year involving a COVID-19 diagnosis, a seized proxy server, and increased complaints of poor card data quality.
The post announcing the shutdown was made on a Russian-language cybercrime forum, where the administrator for Joker’s Stash explained that they are going “on a well-deserved retirement”. The message explains that the marketplace will remain up for a month to allow Joker’s Stash customers to spend their account balances but will ultimately “fade to dark, forever” on February 15, 2021. The admin also warns that they will not be opening again, and other marketplaces using their name would be “imposters”.
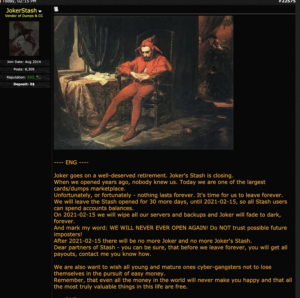 The message announcing Joker’s Stash shutdown
The message announcing Joker’s Stash shutdown
The admin’s post does not explain why they made the decision, though the turbulent year the marketplace had probably had something to do with it. Threat intelligence company Intel 471 revealed that US Department of Justice and Interpol allegedly seized proxy servers that were used in connection with the blockchain-based domains that belong to Joker’s Stash. At the time, the marketplace’s operators were quick to reassure customers that they would quickly return to normal. Furthermore, the cybercriminal running the marketplace contracted COVID-19 in October and spent a week in the hospital. Their absence ultimately impacted the marketplace, with disruption to the forums, inventory replenishments, and other operations. Intel 471 also noted that customers started complaining that the marketplace’s payment card data quality was becoming increasingly poor.
“We are also want to wish all young and mature ones cyber-gangsters not to lose themselves in the pursuit of easy money. Remember, that even all the money in the world will never make you happy and that all the most truly valuable things in this life are free,” the admin of Joker’s Stash ended the closure announcement with a warning.
Emotet botnet disrupted by a global law enforcement operation
On January 27, 2021, Europe’s law enforcement agency Europol disclosed that a joint operation involving law enforcement agencies of eight countries has disrupted one of the world’s most dangerous malware Emotet.
Emotet was initially a banking trojan but a couple of years into its operation it was reconfigured to work as “loader” malware. Initially detected in 2014, by 2016 its operators had it working as malware that could install other malware onto the infected computer. Four years in, Emotet had become a huge network of infected computers (aka a botnet) and was considered to be one of the world’s most dangerous malware. Seeing the potential, Emotet operators also started offering the malware as malware-as-a-service (MaaS). For a price, cybercriminals were able to buy access to Emotet’s network of infected computers, and install their own malware. This was particularly appealing for ransomware operators. The notorious Ryuk ransomware gang were regular clients of Emotet, for example. In the 4 years of operation as a botnet and MaaS, it is estimated that Emotet has caused hundreds of millions of dollars in damages.
The primary means of infection were email attachments. Emotet would be hidden in email attachments disguised as invoices, receipts, shipping notices, documents containing information about COVID-19, etc., and all users had to do to infect their computers is open the attachment and enable macros when prompted. In many cases, the malware would lurk on the computer, waiting to install some malware whose operators bought access to the computers in the botnet.
Because of how dangerous Emotet is, Europol’s news of its disruption is a significant event in cybersecurity. In a press release, Europol reveals that a joint operation involving law enforcement agencies in the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine, has brought down the Emotet botnet. Europol and Eurojust coordinated international activity.
According to Europol, Emotet was more resilient against takedown attempts because it had several hundreds of servers with different functionalities all over the world. Nonetheless, cooperating law enforcement agencies from eight countries were able to take control of the infrastructure and taken down Emotet from the inside.
Two arrests have been made in Ukraine but other people involved in Emotet have been identified and are in the process of being detained. Ukraine’s law enforcement has released a video of the arrest of two individuals who were likely responsible for keeping Emotet’s servers running smoothly.
Emotet’s two primary command and control (C&C) servers were located in the Netherlands, which allowed Dutch authorities to seize a significant amount of data. The Dutch National Police has created a page where people can check whether their email addresses were among the seized data. If the email address was indeed present in the seized data, there is a significant chance that Emotet has been installed on the computer.
Dutch authorities are also planning on delivering an Emotet update that will remove the malware from infected computers. The release should happen on March 25, 2021. In the meantime, infected devices have been redirected to an infrastructure controlled by law enforcement.
References
- Joint Statement by the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Office of the Director of National Intelligence (ODNI), and the National Security Agency (NSA). CISA.
- Marcin Kleczynski. Malwarebytes targeted by Nation State Actor implicated in SolarWinds breach. Evidence suggests abuse of privileged access to Microsoft Office 365 and Azure environments. Malwarebytes News.
- DarkMarket: World’s largest illegal dark web marketplace taken down. Europol Press Release.
- Australian man arrested in Germany over ‘world’s largest’ darknet marketplace. The Guardian.
- Last Dash for Joker’s Stash: Carding forum may close in 30 days. Intel 471.
- World’s most dangerous malware Emotet disrupted through global action. Europol Press Release.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.

