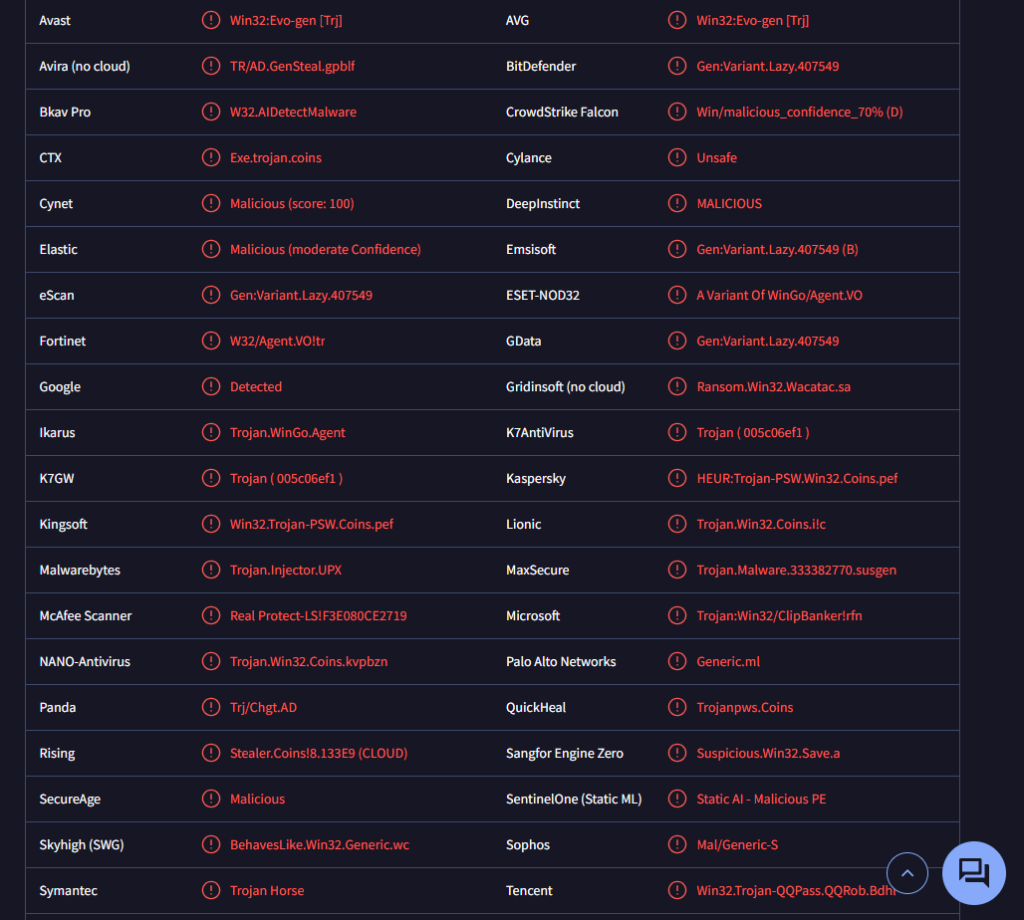
Remove Salat trojan
Salat trojan is a data-stealing type of malware. The reason it’s classified as a stealer type of malware is that it aims to steal highly sensitive information from the infected device. It’s a very serious infection that users will not necessarily notice because it stealthily stays in the background. It has several worrying features, including the ability to steal files and record video as well as audio.
Once the malware is initiated, it immediately starts collecting device data. It primarily targets running processes, opened windows, hard drive details, etc. It will also search for specific processes and will try to extract information related to active windows. One of the trojan’s more worrying features is its ability to record audio and video, as well as live-stream desktops. This may be a serious breach of privacy as users’ private conversations and moments may be recorded. This could allow malicious actors to blackmail victims. What’s more, the malware’s functionality currently includes being able to steal files as well.
Stealer trojans aim to steal as much data as possible, and that means they need to stay in the background undetected. Some malware infections like ransomware immediately make their presence known but others try to avoid detection. Without an anti-malware program, this trojan may remain unnoticed on the device for a long time. There are some signs that indicate malware’s presence (e.g. unknown processes appearing in Task Manager, programs crashing without reason, sluggish computer) but users should generally leave malware detection to the anti-malware program.
Using an anti-malware program to delete Salat trojan is necessary because it’s a sophisticated infection.
How did the Salat trojan infect the computer?
Email attachments are a very common method for distributing malware, and being able to recognize malicious emails is very important if users want to avoid malware in the future. Emails with malicious files attached are often disguised as legitimate communications from reputable companies. When users open these attachments, their devices can become infected. If the malware is designed to steal data and there’s no anti-malware software installed, users might remain unaware of the infection. Generally, these malicious emails are quite generic unless they target specific individuals, which makes them easier to identify. For example, they typically contain numerous grammar and spelling mistakes. Since the senders pose as legitimate companies, these mistakes stand out immediately. A common tactic is to mask the email as an order confirmation or a parcel delivery notice, but the mistakes immediately reveal the malicious intention.
Malicious emails often address recipients with vague terms like “User”, “Member”, or “Customer”. In contrast, legitimate companies personalize emails as much as possible and use customers’ names. Malicious actors, however, typically have only limited access to personal information, which is why they resort to generic words. If, for example, you receive an unsolicited order confirmation that addresses you using generic words, it could indicate a malicious email.
On the other hand, targeted malicious emails are usually much more sophisticated. They target high-profile individuals or companies and often include a lot of details and credible information. They also typically do not have grammar and spelling mistakes and address the recipient by name. Just to be safe, it is highly advisable to scan any unsolicited email attachments using anti-malware software or services like VirusTotal before opening them. This will ensure that you do not open any malicious files that could initiate malicious infection onto your device.
Malware is also commonly spread through torrents. A lot of torrent sites are poorly moderated, which allows malicious actors to upload torrents with malware in them. Especially popular torrents for entertainment content—such as movies, TV shows, and video games—are frequently found to contain malware. Keep in mind that downloading pirated content is not content theft but also poses significant risks from malware threats.
How to remove Salat trojan from your computer
Trojan infections are very serious, particularly data-stealing types. Because they are sophisticated infections, it’s strongly recommended to use an anti-malware program to remove Salat trojan from your computer. In fact, you may not even notice its presence without an anti-malware program. Once you remove Salat trojan using an anti-malware program, we also recommend securing your accounts by changing your passwords and enabling two-factor authentication.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.