Remove Pe32s ransomware
Pe32s ransomware is file-encrypting malware that will encrypt certain files on the infected device. This malware can be recognized by the .pe32s extension it adds to encrypted files. Once files are encrypted, users will not be able to open them unless they first use a decryptor on them. However, getting the decryptor is not going to be easy because only the malicious actors behind this ransomware have it. They will not just give it to you and instead require a payment.
Pe32s ransomware can be recognized by the extension it adds to encrypted files: .[victim’s unique ID].[file format].pe32s. For instance, a file named image.jpg would change to image.[victim’s unique ID].[jpg].pe32s. This ransomware targets personal files such as photos, videos, and documents, as these are the types of files that users are often most inclined to pay to recover. After the files are encrypted, a README.txt ransom note will appear in every folder containing affected files. This note explains that the files have been encrypted and can only be recovered with a special tool. Unfortunately, this is true. The cybercriminals behind this ransomware will offer the decryptor in exchange for a ransom that can range from $700 to $7,000 for individual users, and from $10,000 for companies.
As a general rule, paying the ransom is discouraged since it doesn’t guarantee that your files will be restored. Although the attackers claim that they will send the decryptor upon payment, there’s no assurance they will follow through. Many victims have paid and never received the promised decryptors. While the choice to pay is ultimately yours, it’s essential to consider the risks, especially given that the requested sum is very big.
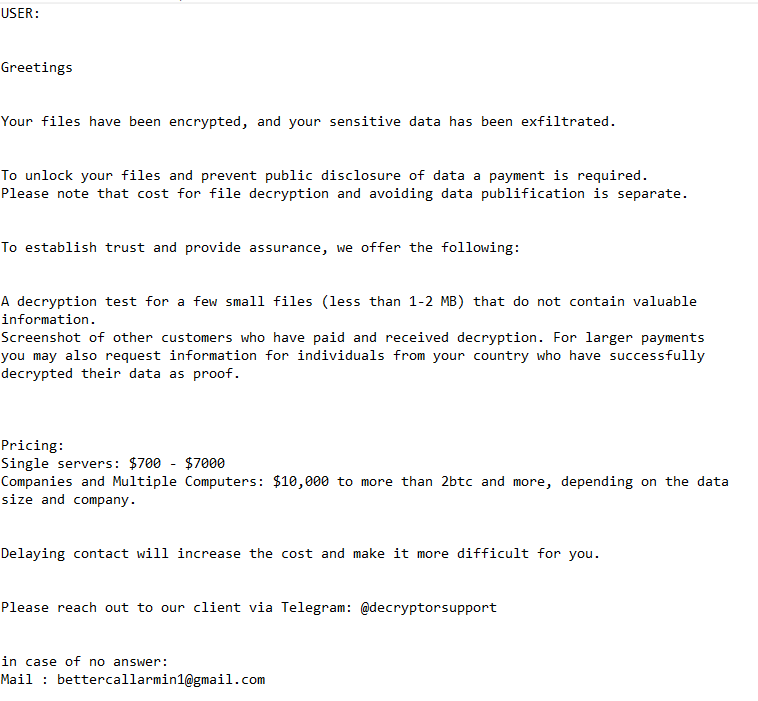
The full Pe32s ransomware README.txt ransom note is below:
USER: –
Greetings
Your files have been encrypted, and your sensitive data has been exfiltrated.
To unlock your files and prevent public disclosure of data a payment is required.
Please note that cost for file decryption and avoiding data publification is separate.To establish trust and provide assurance, we offer the following:
A decryption test for a few small files (less than 1-2 MB) that do not contain valuable information.
Screenshot of other customers who have paid and received decryption. For larger payments you may also request information for individuals from your country who have successfully decrypted their data as proof.Pricing:
Single servers: $700 – $7000
Companies and Multiple Computers: $10,000 to more than 2btc and more, depending on the data size and company.Delaying contact will increase the cost and make it more difficult for you.
Please reach out to our client via Telegram: @decryptorsupport
in case of no answer:
Mail : bettercallarmin1@gmail.com
If you backed up your files before your computer was infected with the Pe32s ransomware, you should be able to recover them without any problems. However, it’s essential that you first remove Pe32s ransomware. If you connect to your backup while the ransomware is still present, those backup files will also end up being encrypted. Do not try to remove Pe32s ransomware manually because you could end up causing additional damage to your computer. Make sure to use a good anti-malware program.
If your files are encrypted by this ransomware, you might have initially searched for a free decryptor. Unfortunately, there isn’t one currently available. We recommend keeping your encrypted files backed up and periodically checking the NoMoreRansom website for updates on decryptors. Be cautious, as there are many fake decryptors advertised on unreliable sites, so make sure to download from trustworthy sources only.
Ransomware infection methods
Users with poor browsing habits are often at the greatest risk of infecting their computers with malware. If you frequently open unsolicited email attachments, download content or software from untrustworthy sources, use torrents, or click on ads while visiting potentially risky websites, it’s only a matter of time before your computer becomes infected with ransomware. Improving your browsing habits is one of the best ways to prevent malware infections in the future.
If you’re using torrents to download pirated content, you might already be aware that torrent sites are usually poorly managed. Malicious actors exploit these sites and upload torrents for popular movies, video games, TV shows, and software with malware in them. While some malicious torrents are easy to spot, others can be quite challenging to identify. Keep in mind that downloading copyrighted content through torrents is not only content theft but also poses a significant risk to your computer and files.
Malicious spam emails, commonly referred to as malspam, are a very common method for spreading infections such as ransomware. Cybercriminals buy large amounts of email addresses from various hacking forums and launch massive spam campaigns. Email addresses end up on these forums following data breaches or leaks. For those whose addresses have been compromised, most malicious emails are fairly obvious. However, when they target specific targets, they may be more sophisticated. Generally, generic malicious emails are riddled with grammatical and spelling mistakes, refer to recipients as “User”, “Member”, or “Customer” and put strong pressure on users to open an attachment, claiming it contains an important document that needs to be urgently reviewed. Generic malicious emails often imitate legitimate correspondence from companies but because they’re very low-effort, they are not difficult to identify as malicious.
However, despite many malicious emails being obvious, it’s still wise to scan any unsolicited email attachments with anti-virus software or services like VirusTotal.
How to remove Pe32s ransomware
Ransomware is a particularly complex form of malware, so we advise against attempting to manually remove Pe32s ransomware. If not done correctly, there is a risk that the malware could recover. Moreover, if it remains on your system and you then connect to your backup, your backed-up files could also become encrypted. Use trusted anti-virus software to delete Pe32s ransomware before accessing your backup files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.